K2 connect for SAP Security Enhancement: SAP SSO Support
KB000689
PRODUCT
Introduction
K2 connect for SAP has been enhanced to support SAP SSO (Single Sign On). This new security feature is provided alongside the existing K2 SSO which offers the client additional choices with regards to security.
Implementation
SAP SSO is offered in conjunction with the existing K2 SSO. In K2 SSO, credentials are cached against the K2 connect security label so that when you execute a BAPI and a request is sent via the K2 Service Object the cached credentials can be used to verify the identity of the logged on user.
How do SAP logon tickets work?
SAP Logon Tickets generate SSO for SAP solutions with Web-based access, that is, for applications that are based on SAP Web Application Server or SAP ITS. A SAP Logon Ticket is used only for the purposes of SSO and cannot be used for initial authentication. To obtain a Logon Ticket, you must first logon using a different procedure, such as a user name and a password or a digital certificate. The Logon Ticket is contained in a cookie that is forwarded to your Web browser by the issuing system. It is forwarded from your browser to the subsequently called systems that are integrated into the SSO landscape. You only log on once. The ticket itself contains your user name, a timestamp, information about the issuing system, and a certain validity period, which can be configured using a system profile parameter, and which can range from a few minutes to several hours. To protect the authenticity and the integrity of the ticket, it is digitally signed by the issuing system. The prerequisite for the use of SAP Logon Tickets is the use of identical user names in the systems that issue and accept the ticket.”
- See the following link for further information SAP Single Sign-On. This resource requires an active, external internet connection
- With K2 connect, you must retrieve the SAP Logon ticket from your Web browser’s session and use it as an input parameter. K2 does not get the Logon ticket. You must implement your own solution for obtaining it and then pass it as a parameter in the K2 connect SmartObject calls for SAP SSO.
Configuration
SAP SSO is available by default from the K2 blackpearl Settings configurations page as shown below. Enable the SAP SSO option and then refresh the service instance by clicking on Refresh Service Instance link on the lower right hand corner of the user page.
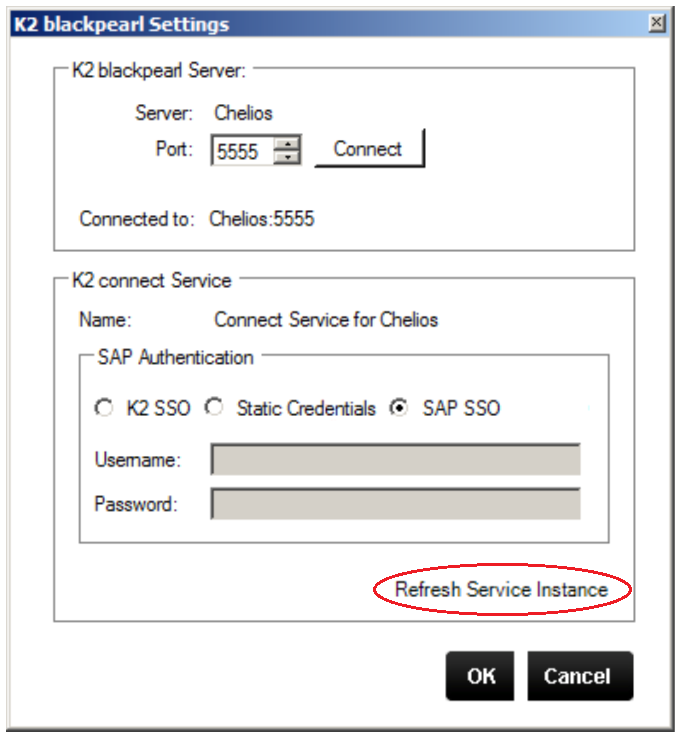
image 1 - K2 blackpearl Settings
Refreshing the service instance is mandatory and affects a change on the system backend by adding a new parameter to the Service Object method called SSO Login Ticket i.e. this is on the SAP side and is visible from within the K2 Testcockpit.
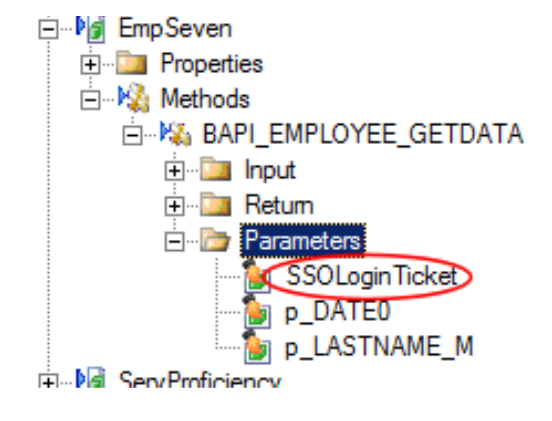
image 2 - SSOLoginTicket
To affect this change, the following must also be done:
- This value needs to be set with the SAP SSO Loginticket whenever a SmartObject is executed
- Any existing SmartObjects will have to be updated to map a parameter to the new SSOLoginTicket parameter
Installation
This update is contained within the latest K2 connect for SAP Update.



