We are excited to announce a significant upgrade to our Single Sign-On (SSO) implementation. We will transition from a third-party vendor to an internally managed service for SSO. This change is designed to enhance your experience by offering improved stability, performance, and flexibility.
Who needs to make this change?
Only SAML federated customers need to perform the upgrade. WAAD federated customers are not affected.
Why are we making this change?
By bringing SSO in-house, we can:
-
Ensure Greater Stability: Control over the service allows us to address issues more quickly and ensure consistent uptime.
-
Enhance Performance: Optimized architecture tailored to Nintex’s environment reduces latency and ensures seamless user experiences.
-
Increase Flexibility: An internal service allows us to respond more effectively to customer needs and implement feature updates at a faster pace.
Additionally, the current third-party solution will reach its end of life in November 2025. This transition not only brings improvements but also ensures continuity and security for your authentication processes.
What do I need to do?
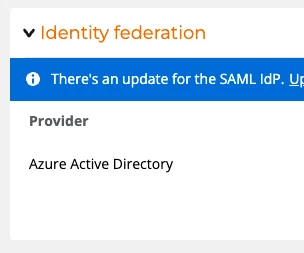
SAML federated customers will need to perform a simple upgrade by changing some values in their Identity Provider. If you need to upgrade you will see a banner on your User Management page under settings:
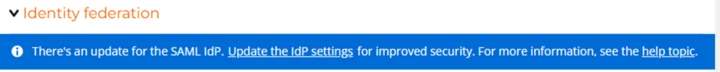
If you select the the ‘...’ beside your identity federation configuration you will see the option to ‘upgrade’ as shown below:
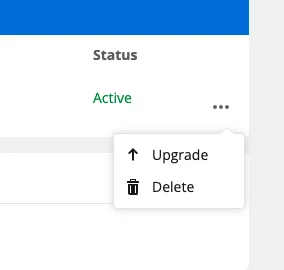
The upgrade process will guide you through the rest of the process where you’ll update the entity ID and ACS URL in your identity provider. You can also view a video demonstration of the upgrade here.
When do I need to do it by?
The current SSO solution will be retired on the 30th of November 2025. We encourage all customers to begin planning their upgrade to the new SSO service as soon as possible. Customers that have not upgraded by the 30th of November 2025 will be unfederated and fall back to OTP.
How can I get help if I need it?
If you require assistance or have any concerns, please contact Nintex support or your Nintex account manager.
Conclusion
This upgrade is a significant milestone in our journey to provide you with the best possible experience. By transitioning to an internally managed SSO service, we’re ensuring that your authentication processes are more stable, efficient, and adaptable than ever before.