Connecting to On-Premises Data from K2 Cloud
KB002939
PRODUCT
Use this article to discover options available for connecting your K2 Cloud environment to data that exists on-premises, such as in a private network or a different cloud environment. Use this data in applications you build in K2 Cloud. Supported on-premises systems include any system with which K2 Cloud has a standard integration capability. However, some sources such as SharePoint are not supported.
This article does not outline the specific steps to implement these approaches. You must review factors such as security, availability, and speed for your individual needs when deciding to implement any of these solutions.
Table of Contents
- Summary of Approaches: Use this section to determine how you want to connect K2 Cloud to your on-premises systems
- Configuring Feature Instances and Service Instances: Once you have a connection, use this section to configure feature and service instances to connect to on-premises systems and services using static credentials
Summary of Approaches
Use one or more of the following approaches and features to access on-premises data from K2 Cloud.
- K2 Cloud On-premises Data Access
- Site to Site VPN
- Opening Network Firewall Ports
- Placing Systems in a DMZ
K2 Cloud On-premises Data Access
This approach allows you to configure a K2 Cloud On-premises Data Access connection from K2 Cloud to your on-premises systems. K2 Cloud On-premises Data Access is a service that enables you to connect line-of-business systems within your on-premises data centers while avoiding some of the inherent complexities of VPN (or other offerings described within this guide).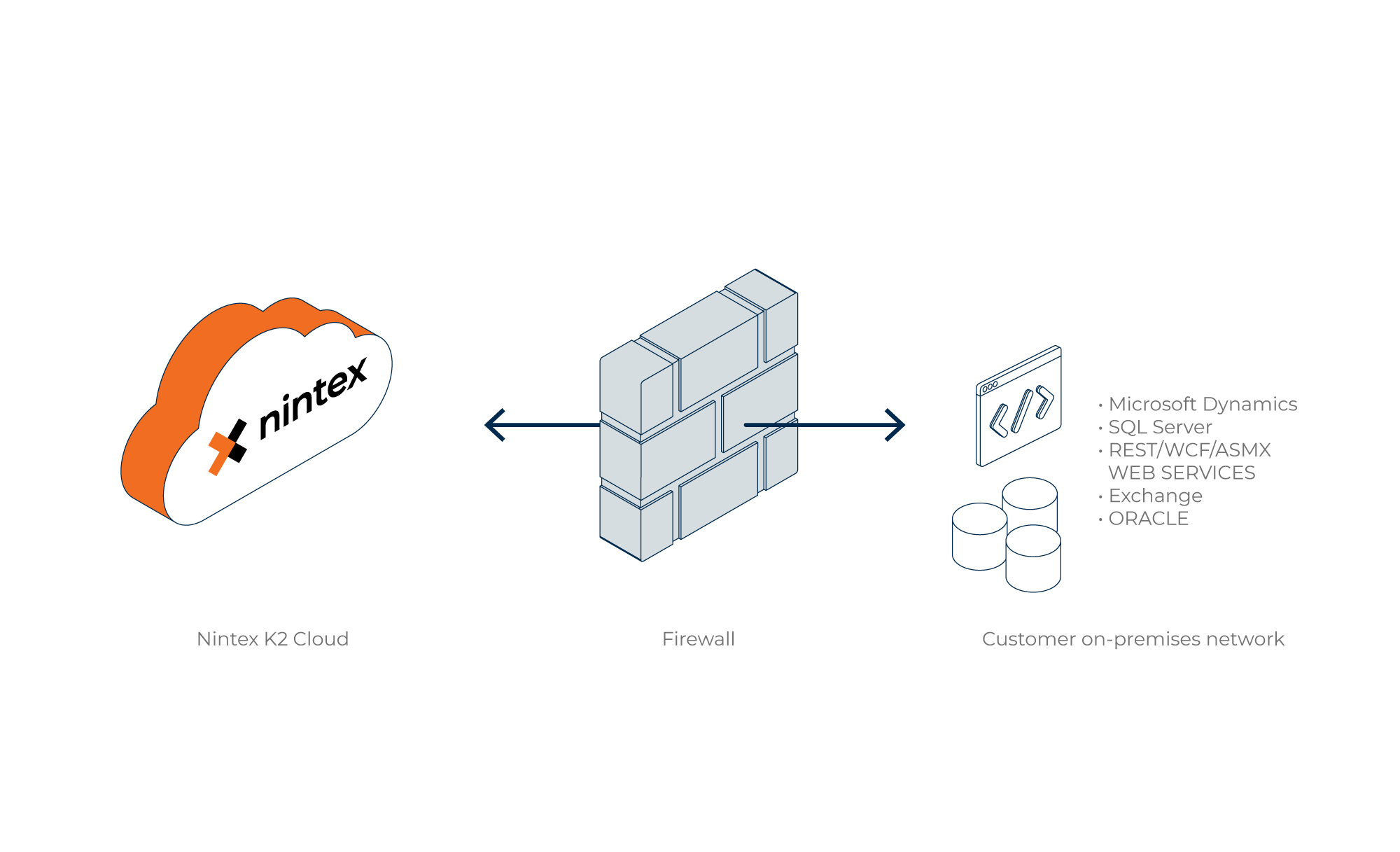
Implementation
For more information about implementing the customer requirements for K2 Cloud OPDA as well as details around deployment, see Configuring K2 Cloud On-prem Data Access.
Site to Site VPN
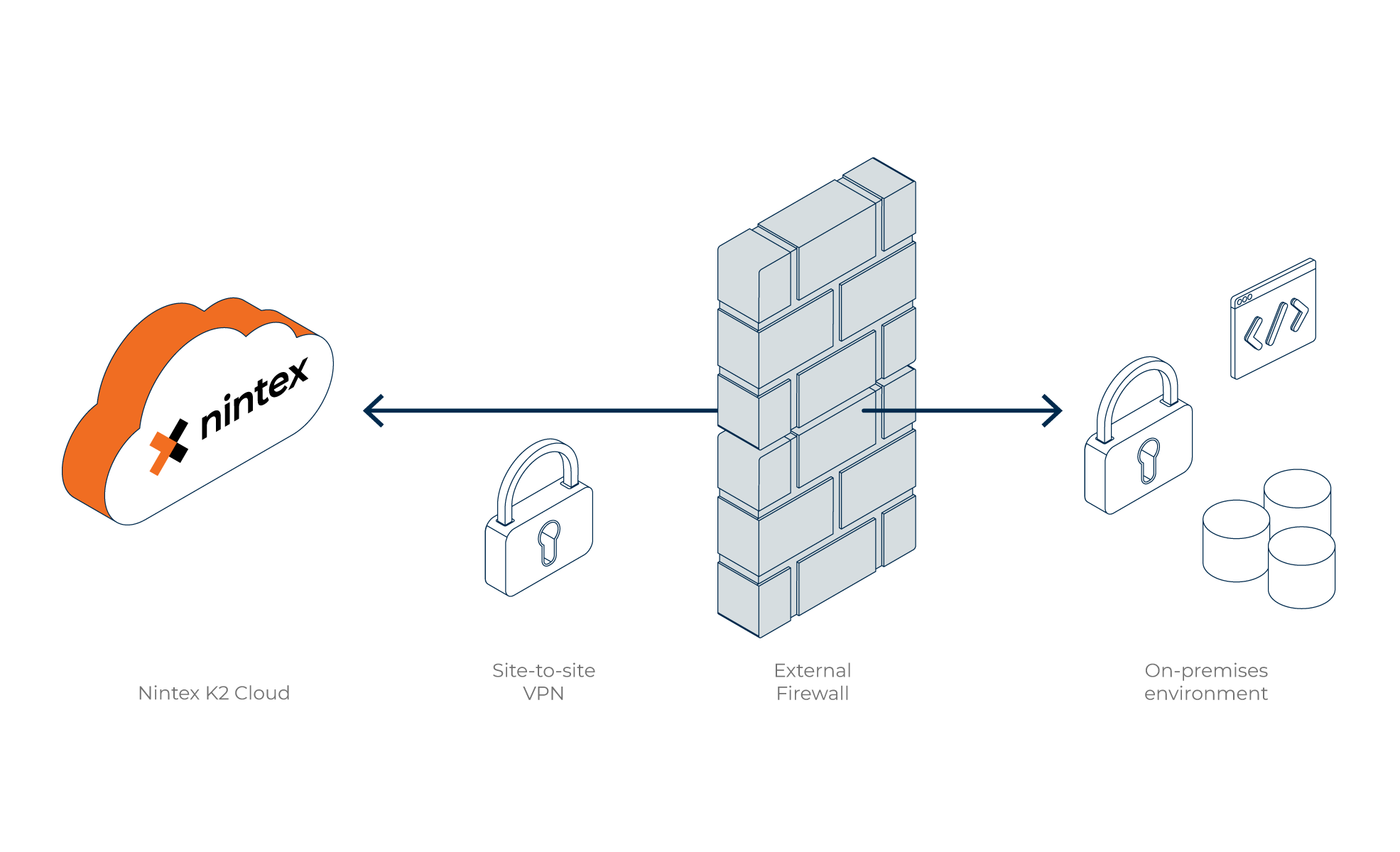
This approach allows you to configure a VPN connection from K2 Cloud to your on-premises systems. Creating and maintaining this VPN connection requires an additional subscription from K2, but you are responsible for configuring and maintaining your on-premises network infrastructure that allows the VPN connection. You cooperate with the K2 Cloud Operations team to configure this approach. Any system that K2 Cloud connects to using this approach must be accessible using DNS or directly by IP address and port. Once you do this you can create a service instance and SmartObjects to use data in K2 Cloud.
Implementation
For more information about implementing a VPN connection from K2 Cloud to your on-premises network, see Configuring a VPN Connection in K2 Cloud. Note that you must work with the K2 Cloud Operations team to configure a VPN connection.
Opening Network Firewall Ports
This approach allows you to selectively open one or more firewalls ports for inbound and/or outbound traffic. If you prefer to not have K2 Cloud applications accessing your systems directly, you can configure a reverse proxy to manage the communication flow between internal data sources and K2 Cloud.
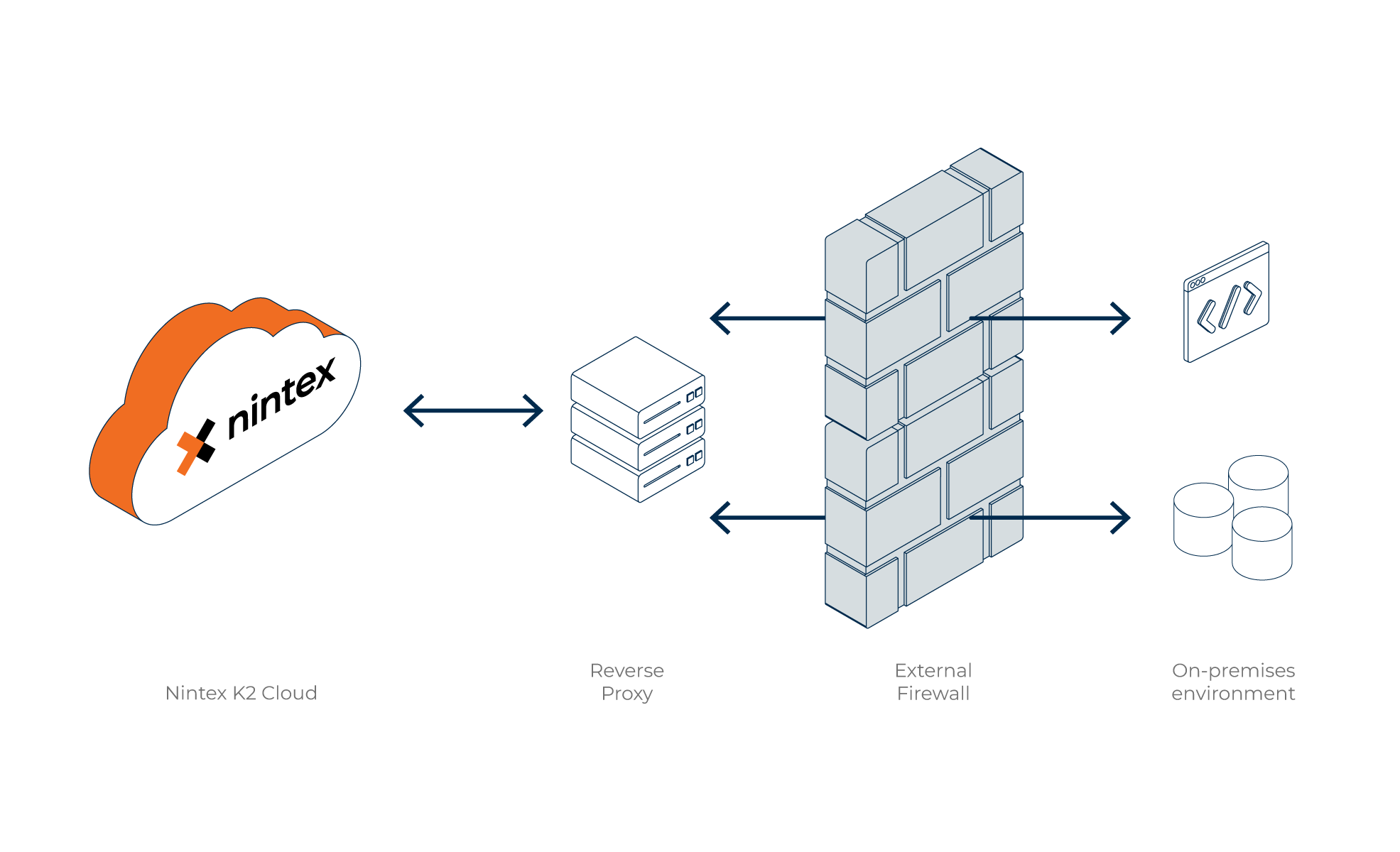
Allowing external systems such as K2 Cloud to your on-premises data by opening firewall ports is a security risk that must be carefully planned and monitored. In many cases, using a reverse proxy provides better security. Also, configuring authentication and whitelisting your K2 Cloud IP addresses is strongly recommended.
Implementation
You are responsible for both networking configuration as well as any additional infrastructure costs to support the security of your on-premises systems. Any system that K2 Cloud connects to using this approach must be accessible using DNS or directly by IP address and port. Once you do this you can create a service instance and SmartObjects to use data in K2 Cloud.
Placing Systems in a DMZ
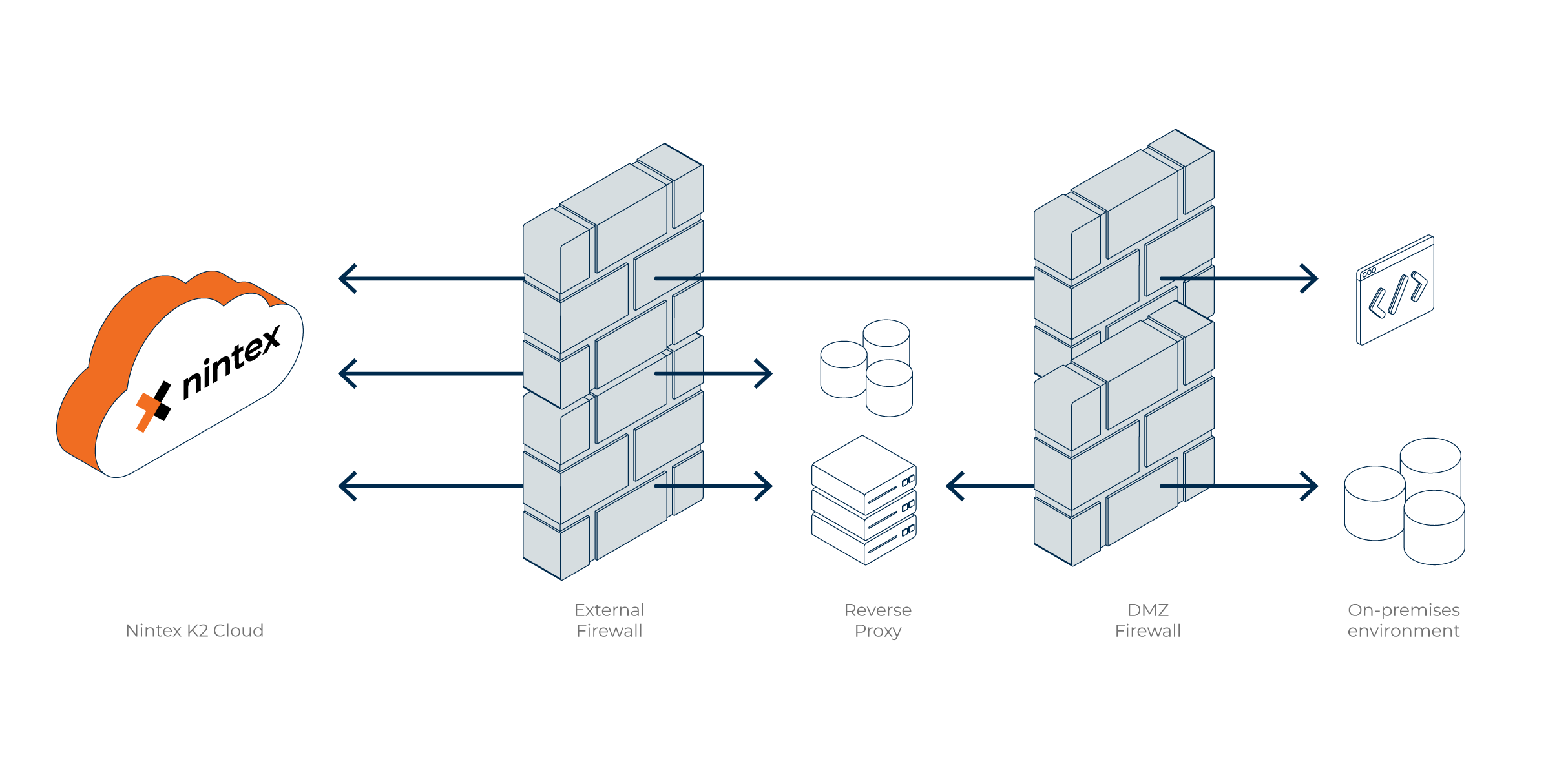
Similar to opening firewall ports, you may choose to locate your data source outside your on-premises in a protected demilitarized zone (DMZ). These systems could be accessed directly by K2 Cloud or with a reverse proxy that manages communication to the data source behind the firewall.
Implementation
You are responsible for both networking configuration as well as any additional infrastructure costs to support the security of your on-premises and DMZ systems. Any system that K2 Cloud connects to using this approach must be accessible using DNS or directly by IP address and port. Once you do this you can create a service instance and SmartObjects to use data in K2 Cloud.
Configuring Feature Instances and Service Instances
Use the information in this section to configure a feature instance or service instance to connect to an on-premises server or service.
Before you configure a feature or service instance, you must have a working, dedicated connection from your K2 Cloud tenant to your on-premises network, using one of the connection options described above.
Microsoft Dynamics CRM
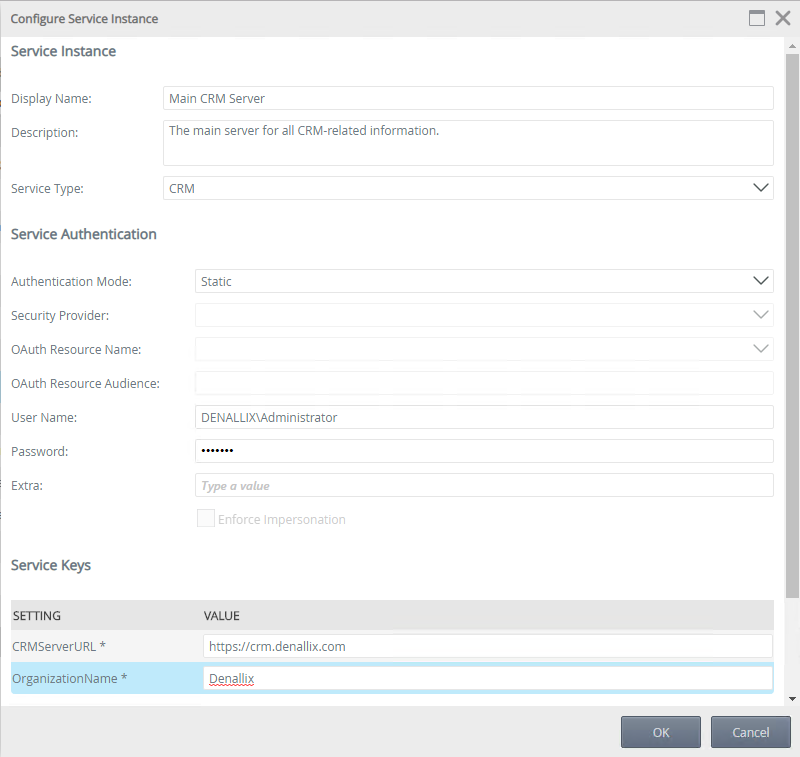
To connect to a Dynamics CRM server using a new CRM service instance, follow these steps:
- Navigate to K2 Management > Integration > Service Types
- Select CRM in the Service Types list and click New Instance
- On the Configure Service Instance page, specify a Display Name and Description (optional)
- Select Static for the Authentication Mode
- Specify a User Name and Password
- Specify your CRMServerURL and OrganizationName
- Your final page should look similar to the following. Click OK to generate the service instance.
- Once the service instance is ready, you can create SmartObjects for that service instance. You can use K2 Designer to manually create advanced SmartObjects, or alternatively:
- Navigate to K2 Management > Integration > Service Instances and select the instance you created
- Click Generate SmartObjects from the toolbar
- On the Generate SmartObjects page, check the Select All option and then click OK to create your SmartObjects
Once created, the SmartObjects are ready to use in your K2 solutions.
You may get the following error when trying to refresh your CRM Online service instance or execute any CRM online related SmartObject:
"An error occurred when processing the security tokens in the message: You are using Ws-Trust authentication which has been deprecated and no longer supported in your environment. Please use OAuth 2.0 authentication."
If you do, make sure you change the Use OAuth Protocol with Static Credentials Service Keys setting to true.
The reason this error is appearing is that Microsoft deprecated the WS-Trust authentication type (also known as Office365 authentication type). You can find more information in the article Deprecation of Office365 authentication type and OrganizationServiceProxy class for connecting to Dataverse.
Microsoft SQL Server
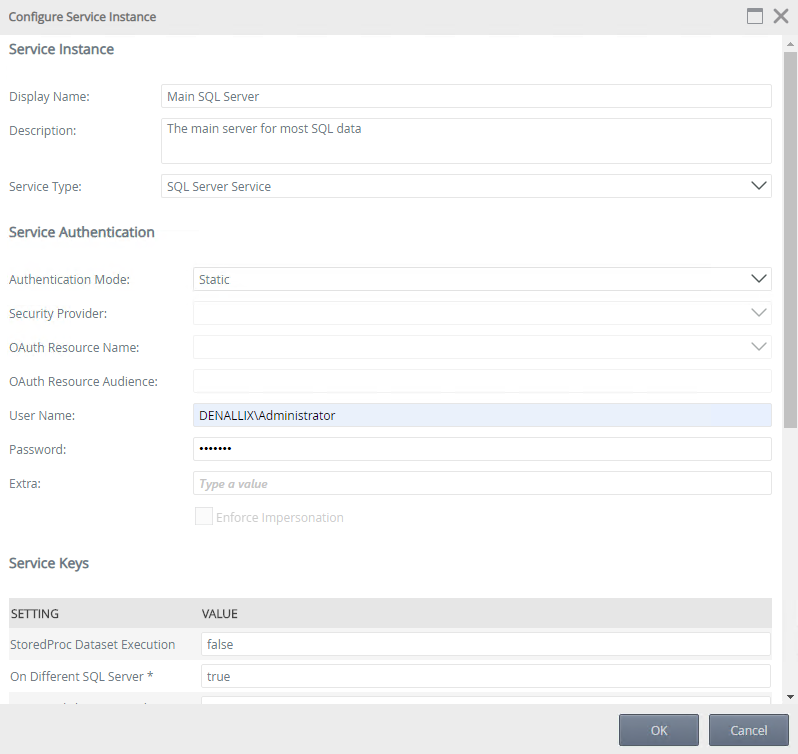
To connect to a Microsoft SQL Server using a new SQL Server service instance, follow these steps:
- Navigate to K2 Management > Integration > Service Types
- Select SQL Server Service in the Service Types list and click New Instance from the toolbar
- On the Configure Service Instance page, specify a Display Name and Description (optional)
- Select Static for the Authentication Mode
- Specify a User Name and Password
- Change the On Different SQL Server service key to true
- Specify a Database and a Server
- Your final page should look similar to the following. Click OK to generate the service instance.
- Once the service instance is ready, you can create SmartObjects for that service instance. You can use K2 Designer to manually create advanced SmartObjects, or alternatively:
- Navigate to K2 Management > Integration > Service Instances and select the instance you created
- Click Generate SmartObjects from the toolbar
- On the Generate SmartObjects page, check the Select All option and then click OK to create your SmartObjects
Once created, the SmartObjects are ready to use in your K2 solutions.
REST/WCF/OData/ASMX Web Services
To connect to a REST, WCF, OData, or SOAP web service using a new service instance of the appropriate service type, follow these steps:
- Navigate to K2 Management > Integration > Service Types
- Select one of the following Service Types in the list below, as appropriate for the service you are connecting to, and click New Instance from the toolbar
- Endpoints WCF
- Endpoints WebService
- OData
- REST
- On the Configure Service Instance page, specify a Display Name and Description (optional)
- Select Static for the Authentication Mode
- Depending on the service you’re connecting to, you may choose to leave the User Name and Password blank or provide values for it if the service requires a login.
- Specify values for the service instance options, such as a Service Endpoint URL and Service Metadata URL for WCF, a WebService URL for WebService, an OData Service URL for OData, or a Descriptor Location for REST.
- Click OK to generate the service instance
- Once the service instance is ready, you can create SmartObjects for that service instance. You can use K2 Designer to manually create advanced SmartObjects, or alternatively:
- Navigate to K2 Management > Integration > Service Instances and select the instance you created
- Click Generate SmartObjects from the toolbar
- On the Generate SmartObjects page, check the Select All option and then click OK to create your SmartObjects
Once created, the SmartObjects are ready to use in your K2 solutions.
Exchange
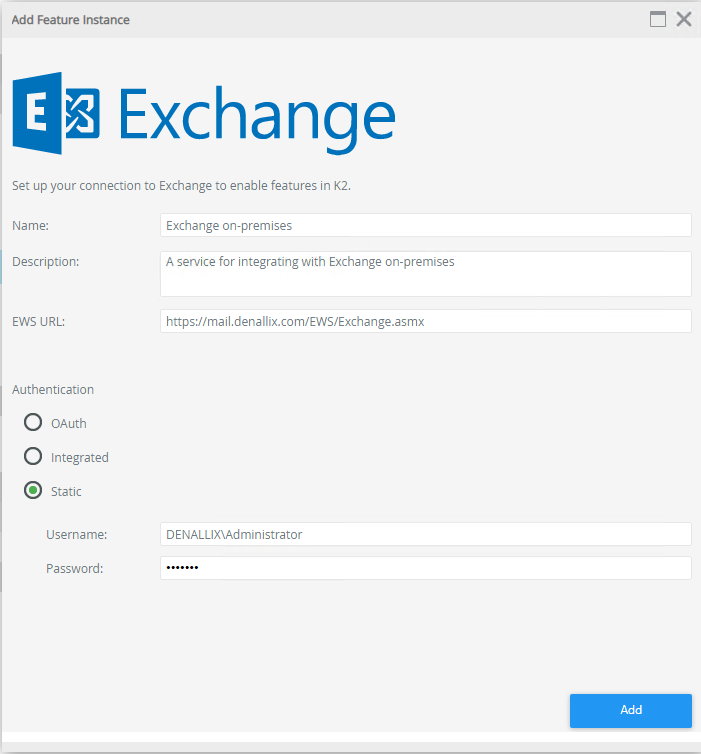
There are two different ways to connect to an Exchange server. The recommended way is to create an instance of the Exchange Online feature (which can also be used to connect to a Microsoft Exchange Server on-premises running Exchange Web Services with the Exchange2013 schema) and use static credentials. To do this, follow these steps:
- Navigate to K2 Management > Features
- Select the Exchange Online feature and click New Instance from the toolbar
- On the Add Feature Instance page, specify a Name, Description, and EWS URL
- Click Static in the Authentication section and specify a Username and Password
- Click Add to create the feature instance
- Once the service instance is ready, you can create SmartObjects for that service instance. You can use K2 Designer to manually create advanced SmartObjects, or alternatively:
- Navigate to K2 Management > Integration > Service Instances and select the instance you created
- Click Generate SmartObjects from the toolbar
- On the Generate SmartObjects page, check the Select All option and then click OK to create your SmartObjects
Once created, the SmartObjects are ready to use in your K2 solutions.
The other method of connecting to an Exchange server on-premises is to configure an instance each of the Exchange Management, Exchange Administration, and Exchange Metadata services. If you choose this method, configure the authentication of the service instances as Static with a User Name and Password.
Oracle
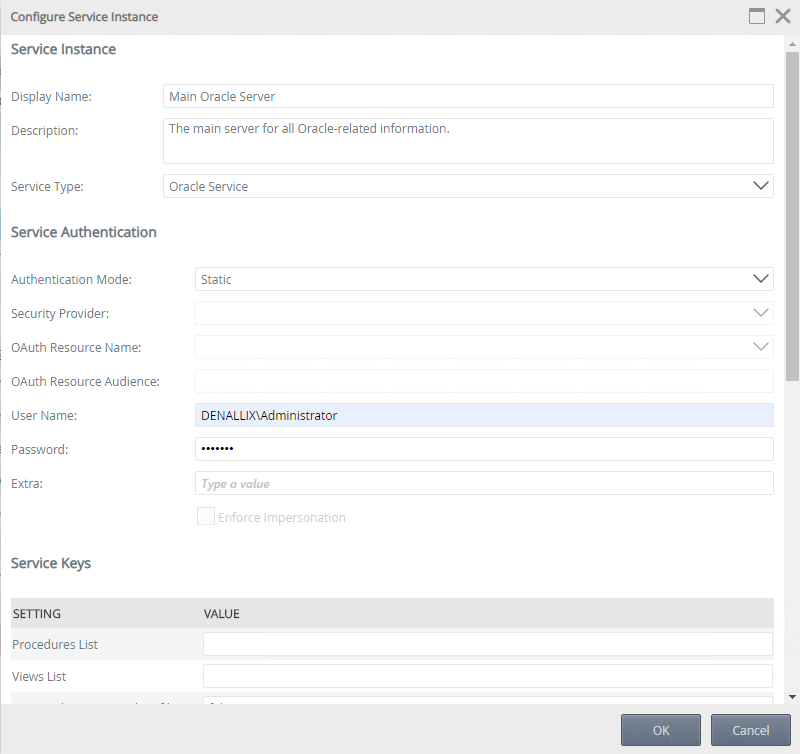
To connect to an Oracle server using a new Oracle service instance, follow these steps:
- Navigate to K2 Management > Integration > Service Types
- Select Oracle Service in the Service Types list and click New Instance from the toolbar
- On the Configure Service Instance page, specify a Display Name and Description (optional)
- Select Static for the Authentication Mode
- Specify a User Name and Password
- Specify values for the Owner List and Connection String. You typically use the same identity information as in step 5.
- Specify values for the required Oracle service keys, including Get Views, Get Procedures, Decimal Precision and Scale, Complex output as XML, Get Packages, Get Tables, and Get Functions.
- Your final page should look similar to the following. Click OK to generate the service instance.
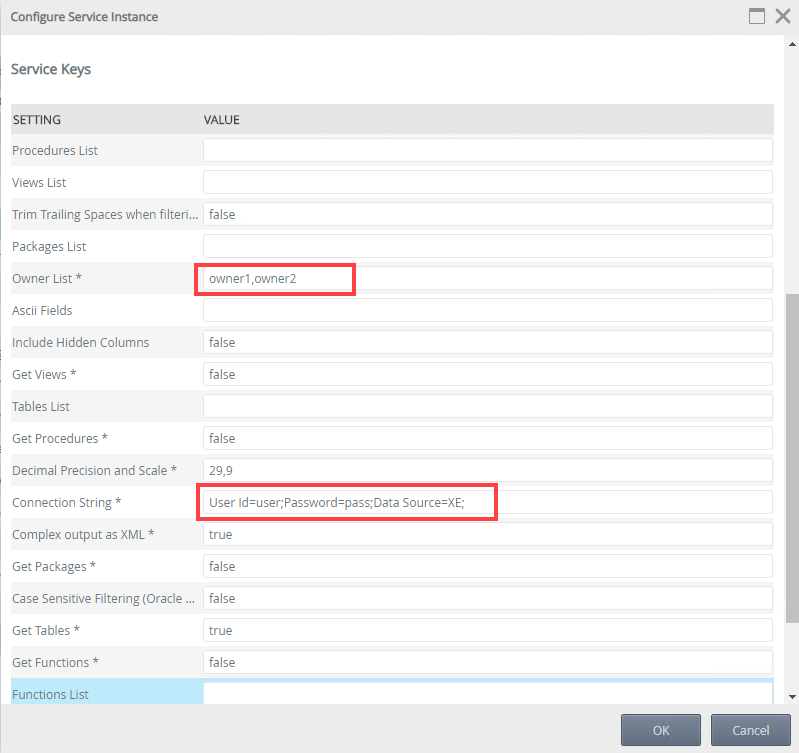
- Once the service instance is ready, you can create SmartObjects for that service instance. You can use K2 Designer to manually create advanced SmartObjects, or alternatively:
- Navigate to K2 Management > Integration > Service Instances and select the instance you created
- Click Generate SmartObjects from the toolbar
- On the Generate SmartObjects page, check the Select All option and then click OK to create your SmartObjects
Once created, the SmartObjects are ready to use in your K2 solutions.



