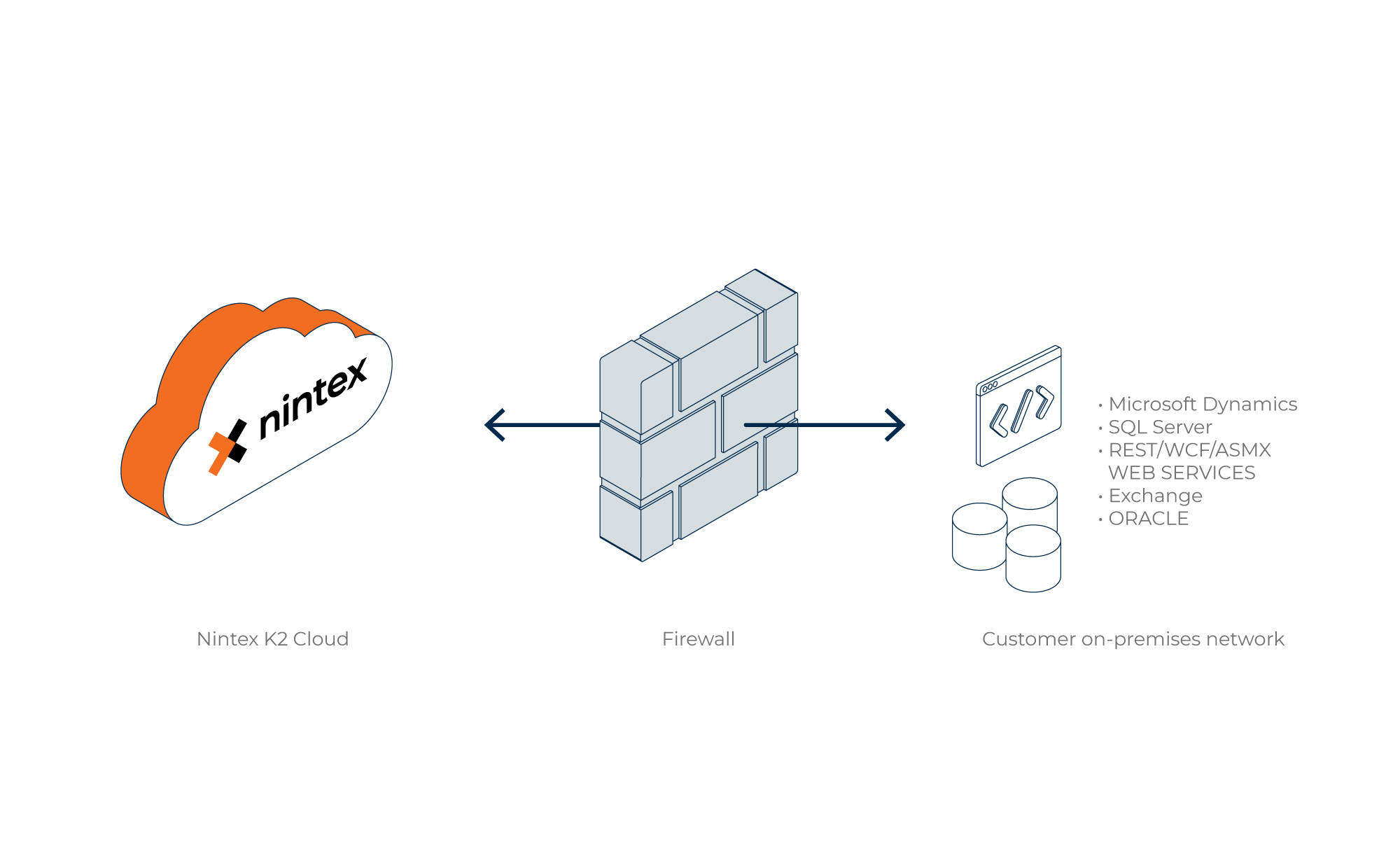
K2 Cloud On-premises Data Access (OPDA) enables you to access your traditional, on-premises line-of-business systems from K2 Cloud applications without the need to place systems outside the firewall or create VPN connections. Data that resides in your on-premises line-of-business systems are made available to your K2 Cloud tenancy using a network appliance deployed within your private network, and are secured by an SSL-based, encrypted, and exclusive connection between your on-premises environment and your tenancy.

For other options when connecting K2 Cloud to on-premises systems, see Connecting to On-Premises Data from K2 Cloud.
Overview
Traditional approaches to connecting on-premises and cloud platforms require complex VPN structures, expensive dedicated circuits, or solutions that require publicly exposing certain network communication ports. These solutions create larger surface areas for data leakage and security breaches in your organization.
K2 On-premises Data Access (OPDA) utilizes a patented, reverse-access technology that does not require a VPN, DMZ or other network infrastructure changes in your on-premises environment.
Accessing On-Premises Systems
K2 OPDA provides integration with the following on-premises line-of-business systems compatible with K2 Cloud. For the latest compatibility information, see Product Compatibility, Integration and Support.
- Microsoft SQL Server 2014, 2016, and 2017
- Microsoft Dynamics CRM 2013, 2015, and 2016
- Microsoft Exchange 2013 and 2016
- Oracle 11g (releases 1 & 2) and 12c
- REST web services
- WCF web services
- SOAP web services
- OData web services
Deployment
K2 OPDA is deployed as a matched pair of nodes: a Connector node, and a Gateway node. You deploy the connector node in your on-premises environment as a virtual machine that is automatically paired to your K2 Cloud tenant, while the gateway node is deployed by K2 Operations in your K2 Cloud tenant environment.
Once you pair the nodes, an encrypted and exclusive tunnel is used between the nodes that allows traffic to flow from your K2 Cloud tenant to the on-premises connector. The OPDA connector ensures that requests to on-premises systems can only be received and fulfilled by the OPDA gateway if that request originated from within the paired node in your K2 Cloud tenant.
Gateway (K2 Cloud environment node)
Located in the organization's K2 Cloud tenant, the role of the gateway OPDA node is to act as a front-end to all applications and users within K2 Cloud. The OPDA Gateway facilitates connections from a customer's supported K2 Cloud SmartObjects to their registered on-premises LOB systems via a secure tunnel established between the customer's K2 Cloud instance and their on-prem connector.
Connector (On-Premises node)
The role of the connector OPDA node is to facilitate secure connections between the gateway within a customer’s K2 Cloud tenant and their on-premises LOB systems.
The connector only responds to valid, inbound requests that originate from the paired OPDA gateway and can only connect to on-premises LOB systems that are designated by the customer.
The connector is deployed as a virtual appliance (VM) that supports Windows Server and Linux distributions.
Security
K2 Cloud OPDA isolates applications and APIs from external attackers, effectively making internal data invisible on the internet while providing the ability to build K2 Cloud apps to integrate with your on-premises line-of-business systems. To protect your on-premises environment, K2 Cloud OPDA provides the following layers of security protection:
- Traffic coming into the on-premises environment from the K2 Cloud OPDA gateway can only originate from the corresponding paired node
- The external K2 Cloud OPDA node does not persist or store any data from requests to or from on-premises systems
- Eliminates opening any standard incoming ports on the internal firewall for client requests to reach line-of-business servers
- Provides layer 3/4 (IP/TCP) attack protection
- Provides fine-grained access control and security policies to limit access to line-of-business servers
See Also
For more information about K2 OPDA, see Overview, Installation, and Configuration of K2 On-premises Data Access.



