K2 and TLS 1.2 & 1.3 Support
KB002500
PRODUCT
Introduction
With the PCI Security Standards Council's move to Transport Layer Security (TLS) 1.2 on the 30th of June, 2018, various 3rd-party providers are disabling the use of older TLS and SSL protocol versions in their products.
K2 integrates with many 3rd-party providers such as Microsoft SharePoint, DocuSign, and SalesForce. With the PCI move to TLS 1.2, when a K2 solution is integrated with these providers and the system in which K2 resides is NOT configured for TLS 1.2, possible communication errors may occur. All machines running K2 components (for example, K2 server, K2 websites) require Transport Layer Security (TLS) version 1.2.
From Nintex Automation (5.8.1) the product now fully supports TLS 1.3 and has moved to using SystemDefault Enum instead of hardcoding the TLS version. This ensures that the best available TLS version is negotiated based on the system’s capabilities. No additional configuration is required in most cases—if the infrastructure supports TLS 1.3, it will be used automatically. TLS 1.3 is currently only supported by Windows 11 and Windows Server 2022. For more information, see this article: Protocols in TLS/SSL (Schannel SSP)
Requirements for TLS 1.3 Compatibility
With full TLS 1.3 support now implemented, the following requirements must be met to ensure seamless functionality:
- K2 (all components) must be installed on a Windows Server 2022 or later machine with only TLS 1.3 enabled for server connections.
- Note: While SQL Server supports TLS 1.3 and can communicate over it, TLS 1.2 must also remain enabled for supporting services to start up successfully. If TLS 1.2 is disabled on your K2 system, SQL Server will not function correctly. To ensure compatibility, both TLS 1.2 and TLS 1.3 should be enabled on the same machine. See TLS 1.3 Support for more information
- Major supported browsers must be able to connect to SmartForms from a different machine.
- While only Windows 11 fully supports TLS 1.3, major browsers support it even when installed on an older Windows version.
- All web-based brokers must successfully connect to their respective services when those services enforce TLS 1.3 only.
- K2 must be able to establish outbound TLS 1.3 client connections when its host machine enforces TLS 1.3, even if the external services support both TLS 1.2 and TLS 1.3.
Important Note: If a service only supports TLS 1.2, while the K2 server enforces TLS 1.3 client connections, the connection should fail, confirming correct behavior.
Configuring TLS 1.2
K2 runs under the .Net 4.6 runtime, which fully supports TLS 1.2, for both server (inbound) and client (outbound) connections.
If the server on which K2 is installed is not correctly configured for TLS 1.2, errors may occur. Below is an example of an error that may occur when TLS 1.2 is not configured correctly:
The underlying connection was closed. An unexpected error occurred on a send.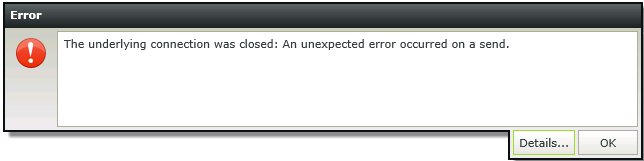
To avoid these issues you have two options:
- Minimum Requirement: Make sure that the K2 server can communicate with other services that only allow TLS 1.2
- Maximum Protection: Force the entire server to only allow TLS 1.2 connections so that incoming and outgoing connections use this higher level of security
Editing the registry incorrectly can cause system instability or crashes. You should back up the registry before making any changes, and you should be familiar with editing the registry before adding or modifying these keys.
Once you make these changes you need to restart the entire server for them to take affect.
Minimum Requirement
To implement the minimum requirement, add or edit the following keys in your K2 server's registry:
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727] |
| Value | SystemDefaultTlsVersions |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727] |
| Value | SystemDefaultTlsVersions |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] |
| Value | SchUseStrongCrypto |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] |
| Value | SystemDefaultTlsVersions |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319] |
| Value | SchUseStrongCrypto |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319] |
| Value | SystemDefaultTlsVersions |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000001 |
Maximum Protection
To implement the maximum protection for all .NET apps on the K2 server, including K2, configure all settings as listed in the minimum requirements section above, and then also add or edit the following keys in your K2 server's registry:
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNELProtocols\TLS 1.1\Client] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000001 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] |
| Value | DisabledByDefault |
| Data Type | DWORD |
| Data | 00000000 |
| Registry Path | [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Security\Providers\SCHANNEL\Protocols\TLS 1.2\Server] |
| Value | Enabled |
| Data Type | DWORD |
| Data | 00000001 |
Considerations
- If you see errors like Initialization failed before PreInit: Membership could not be verified: A connection was successfully established with the server, but then an error occurred during the pre-login handshake. (provider: TCP Provider, error: 0 - An existing connection was forcibly closed by the remote host.), it might mean that one of the app pools used for a K2 site is still set to use an earlier version of the .NET framework. Use IIS Management to identify the .NET version associated with App Pools linked to the K2 sites. You may find it necessary to set these App Pools (K2_net4) to use a later version of .NET (e.g. .NET 4.0) that supports TLS 1.2+ The legacy K2 Web Service components App Pool (K2) must run on the .NET CLR version v2.0.50727. Changing this will cause issues.
- SQL TLS 1.2 Limitation: SQL Server still requires TLS 1.2 to start up. If SQL is running on the same VM, TLS 1.2 cannot be disabled.
- .NET Registry Settings: The version of TLS that .NET uses can be configured or limited via registry settings. If you experience issues, you should check your registry settings to ensure TLS 1.3 is not restricted. See Protocol settings for more information
- Infrastructure Compatibility: If you experience compatibility issues, you should verify your OS, .NET version, and registry settings, and check whether any group policies or security configurations enforce specific TLS versions.



