Troubleshooting the K2 Task List App (Sync Services)
KB001592
PRODUCTHow to work with K2 Mobile Task Lists
TAGS
Introduction
| Note: This topic refers to deprecated products, components or features that K2 no longer supports. This topic is offered "as is" and will no longer be updated. Starting with K2 4.7 the latest K2 Mobile apps must be used. |
The K2 Mobile applications, regardless of the mobile platform, all depend on the K2 Sync Services in order to interact with the K2 worklist. The following article discusses several troubleshooting tips and things to check if you are experiencing issues with the K2 Mobile applications.
Configuring K2 Services to Enable Mobile Connectivity
To support the mobile applications you must expose the SyncREST.svc endpoints included in K2 Services on your extranet. The current mobile applications support basic authentication, with or without SSL encryption. See below for more information.
| Important: Basic authentication is inherently insecure over non-SSL transports (usernames and passwords are sent in clear text); as such, the SyncREST.svc endpoints are configured by default to use Basic Authentication with SSL. In order to use Basic authentication, SSL for the website should be configured. Disabling the SSL requirement for Basic Authentication is provided for development purposes only. |
Configuration of the SyncREST.svc endpoints is done by modifying the web.config file, located at <install drive>:Program Files (x86)K2 blackpearlWebServicesK2Services. For more information about configuration options, refer to the Help topic Developer Reference > Services Reference > K2 Services > Configuration
You can use these services from the application server where K2 is installed. If you have K2 blackpearl installed, you can install the services on a different server in your DMZ or extranet environment by installing the K2 Workspace on the secondary server. If you have K2 blackpoint installed, having the services on a different server in your DMZ or extranet environment is not supported.
Changing the default security label on Sync services
If using other security providers such as SQLUM, LDAP or even custom, you need to comment out the "defaultSecurityLabel" attribute in the Web.config file: 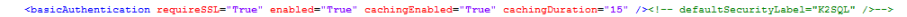
Also, when supplying the username in the settings for the task list, the format must be "label:user". For example:
- K2SQL:superuser
- K2:K2WorkflowDavidg
Known Issues
The default K2 task pages for SharePoint Workflow Integrated (SPWI) processes are not enabled for the mobile rendering engine in SharePoint. To bypass the SharePoint mobile rendering engine and open the K2 task forms directly on your device you must disable the SharePoint Mobile Redirection System. For more information see, http://social.technet.microsoft.com/Forums/en-US/sharepointgeneralprevious/thread/c71cc609-aea5-44f7-9945-8ba9dd85e099/. Please note that InfoPath, Custom and Default Client Event forms work as expected with this release.
Troubleshooting Connectivity
| The installation will add the folder, 'k2api' to the root of the K2 website. The 'k2api' folder needs to be exposed by the Firewall for users to be able to log in. |
If you cannot connect to the K2 Server using the K2 Task List, try the following items before contacting support.
BlackBerry Application
The K2 Task List uses Direct TCP when BES and WiFi are not available. For Direct TCP to work, you will have to enable and specify APN settings. To check this, perform the following steps:
- Open the phone options
- Go to Advanced Options > TCP/IP
- Enable APN and enter the access point name. Optionally configure a user name and password. You will have to contact your service provider if you do not know these settings.
Server and Firewall Configuration
Connection Port
This depends entirely on how the firewall is set up. If the firewall is set up as recommended this can be omitted (as 443 is the default port for HTTPS traffic).
Firewall Setup
These are recommended values and assume ports in IIS have not been changed from the installer defaults. In all cases the firewall should only match requests for “[scheme]://[domainname]/K2Services/*” (where [scheme] is HTTP or HTTPS, [domainname] is the public DNS name and * is any amount of characters).
For the recommended case you will need to configure SSL in IIS yourself (the installer does not do this). Additionally, it is the supported configuration you can use if TMG does not support encrypting traffic on behalf of internal services.
| External | Requirements | Destination | Destination | Destination | Remarks |
| 443 | Encrypted HTTPS Traffic (SSL/TLS) | IIS that hosts K2 Services | 443 | HTTPS/SSL/TLS | Recommended. Use SSL for both external and internal traffic. |
| 443 | Encrypted HTTPS Traffic (SSL/TLS) | IIS that hosts K2 Services | 81 | Unencrypted | Recommended only if the network channel between K2Services and TMG is considered secure. |
Using K2 Services over an unencrypted channel is breaching security: credentials are exchanged in plain-text and will almost certainly be intercepted and used to breach your network. Make sure that you use SSL for K2Services when interacting with it over the public internet. We recommend that you purchase your certificate from a reputable Certification Authority to maximize compatibility across devices.
For a general guide to Firewall ports and K2, please see the article K2 and Firewalls (KB001318).
External Access
A DNS record in a public nameserver with an A (or AAAA) record that points at your IP address. It is assumed that your IP address is static (DDNS could be used, but is not reliable), if your IP address is not static you will need to purchase a static IP from your ISP who may also be able to provide you with DNS services.



