How to manually reconfigure K2 for AAD using Microsoft Graph API
KB003662
PRODUCTThis article is only relevant to the following cumulative updates:
- Nintex K2 Five (5.5) with the November 2021 Cumulative Update
- Nintex K2 Five (5.4) with the November 2021 Cumulative Update
- Nintex K2 Five (5.3) with the January 2022 Cumulative Update
- Nintex K2 Five (5.2) with the June 2022 Cumulative Update
- Nintex K2 blackpearl (4.7) with the March 2022 Cumulative Update
If you have installed one of these cumulative updates, and intend to upgrade your system to either K2 Five (5.4) or (5.5), you must only use one of these product builds:
Using any other product builds will render your K2 installation unusable.
Microsoft is deprecating Azure AD Graph API in June 2022, and as of June 30th, 2020, stopped adding new features to the API. See these Microsoft articles for more information:
- Migrate Azure Active Directory (Azure AD) Graph apps to Microsoft Graph
- Azure Active Directory (Azure AD) Graph to Microsoft Graph migration FAQ
Microsoft strongly recommends upgrading to Microsoft Graph API to access Azure AD APIs as well as APIs from other Microsoft services. K2 OAuth resources requiring access to the https://graph.windows.net API (AAD Graph), must be upgraded to use https://graph.microsoft.com (Microsoft Graph) as part of the migration from AAD Graph to Microsoft Graph. The Cumulative Updates mentioned at the top of this article include the code fixes necessary for this migration.
This article provides a script that will migrate your AAD Security Provider from AAD Graph to Microsoft Graph so that your access to Microsoft services is not interrupted. The script converts your AAD Security Provider from AAD Graph to MS Graph even if you created a custom provider using AAD.
Do not run this script if you have not updated your K2 system using the relevant update package.
Warning: Do not modify any database definition or database content unless specifically instructed to do so by Nintex. No changes to the K2 Database definition or content are supported unless specifically instructed by Nintex.
Procedure
Follow these steps to migrate your AAD Graph environment to MS Graph.
- Install the correct Fix Pack / Cumulative Update for your system.
- Run the attached SQL script.
- Restart the K2 server.
- In Azure, add the same API permissions for MS Graph as you had for AAD Graph (delegated: Directory.Read.All and User.Read, application: Directory.Read.All). Then revoke the AAD Graph permissions as they are not needed after the migration. See the Azure API permissions section of this article for an example. For more information regarding your app in AAD see step 2 of the topic Manually Configure K2 for AAD.
- If you already have a configured AAD Service Instance, update it's OAuth resource audience using the information in this article: Admin consent recommended before upgrading K2 Five versions.
- You should be redirected to a site to grant admin consent. If this does not happen automatically, edit the {YourTenantID} in this URL then browse to it and perform the consent flow:
https://login.microsoftonline.com/{YourTenantID}/oauth2/authorize?client_id=57928c92-7074-45f8-b89e-fe2556ac187f&response_type=code&redirect_uri=https://help.nintex.com/en-US/HELP_DOC/AADpages/AADSuccess.html&resource=https://api.k2.com&prompt=admin_consent - Open a command prompt and perform an iisreset.
- Test that the migration was successful by using the AAD SmartObject to retrieve a list of users from AAD. If users are returned like before you ran the script, the migration was successful.
Azure API permissions
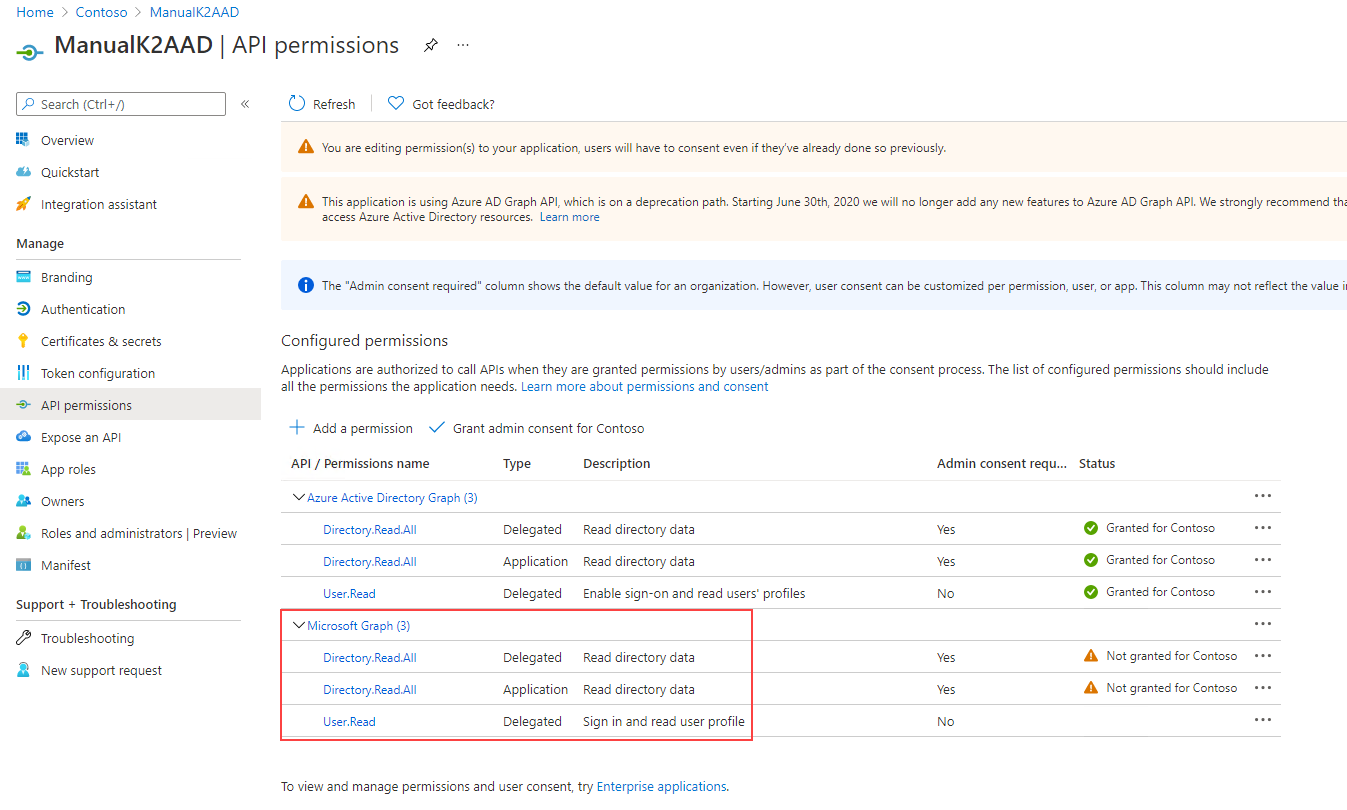
- In Azure, navigate to your app and add the new Microsoft Graph permissions to match what you had for the Azure Active Directory Graph permissions:
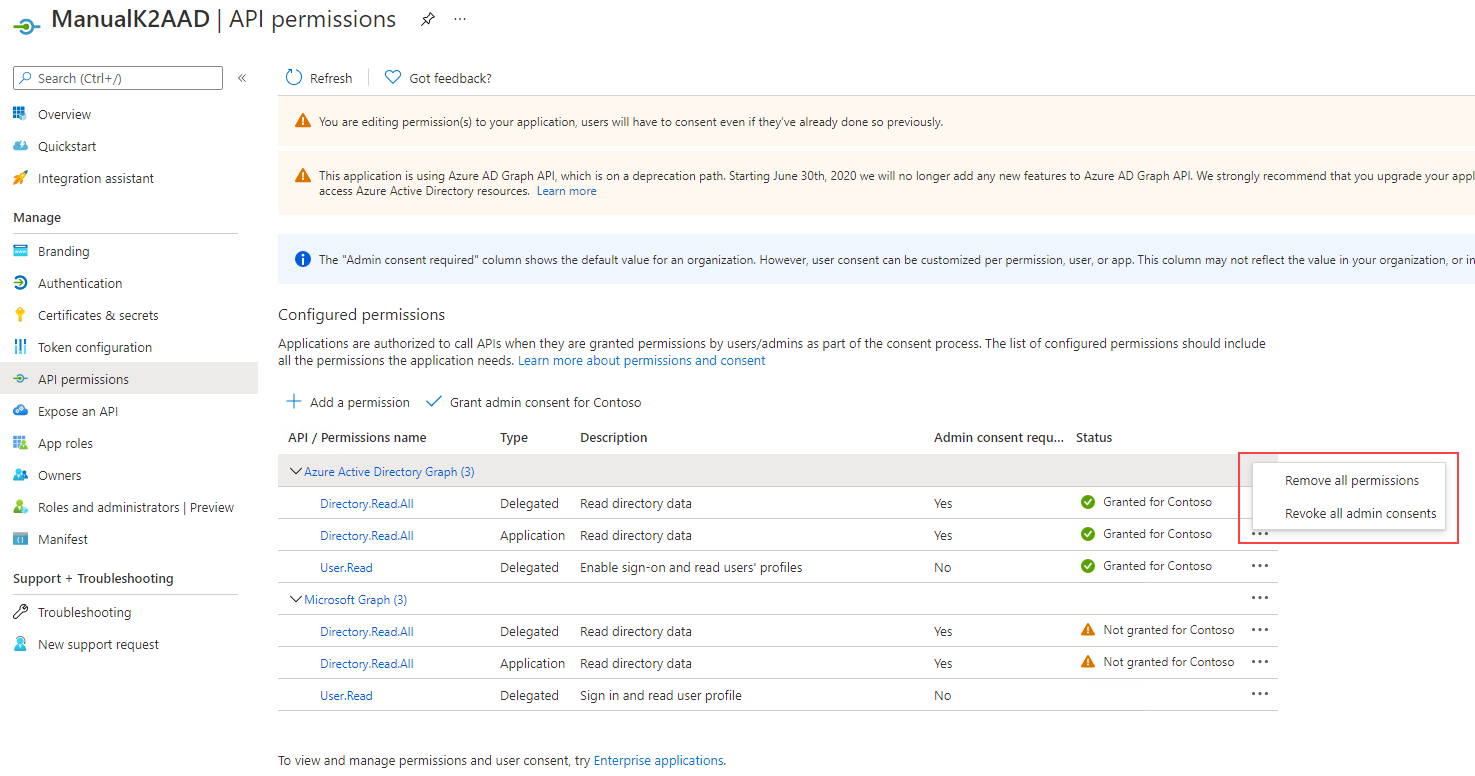
- Once the new permissions have been added, click the ellipse and revoke admin consent, and then remove permissions:
Also see:

