PDF Converter Server-Side Request Forgery Prevention Configuration
KB003666
PRODUCTIntroduction
A server-side-request-forgery (SSRF) risk was identified in the Save as PDF control and the underlying PDF Converter SmartObject, which allows interacting with and discovering internal endpoints.
For added security, you can now configure the PDF Converter to restrict which hosts and IP addresses it is allowed to load any type of resource from.
Resources include, but are not limited to:
- Iframes
- Images
- Style sheets
- Scripts
The configuration options apply to the main URL requested to be converted into PDF, and any resource within the site’s HTML. All HTTP requests that are made as part of the PDF conversion are validated against this configuration. This applies to iframes and the resources within the site that the iframe is for.
Use the guidance below to configure your environment to prevent SSRF. Each environment and solution is different and requires unique settings. If you don’t configure these settings, your environment is still at risk of SSRF.
Configuration
Use the appsettings.xml file found in [Program Files]K2K2 PDF Converter Service to configure your environment’s settings in the NetworkSecurityFilterSettings section as shown below.
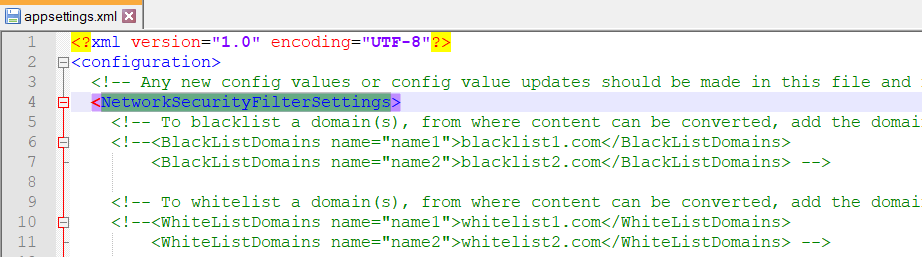
- By default, the configuration allows all requests
Use the table below to determine the settings you need to configure for your environment. Note that not all these settings are required. An administrator should choose which one, or combination of these settings is best in your environment.
| Node | Example | Description |
| BlackListDomains | <BlackListDomains name="name1">internal.denallix.com</BlackListDomains> *See note |
Combining this setting with the BlackListIPAddresses, BlackListSubnets or any of the WhiteList settings is more effective. |
| WhiteListDomains | <WhiteListDomains name="name1">k2.denallix.com</WhiteListDomains> *See note |
|
| BlackListIPAddresses | <BlackListIPAddresses name="name1">10.1.3.15</BlackListIPAddresses> |
Combining this setting with the BlackListDomains, BlackListSubnets or any of the WhiteList settings is more effective. |
| WhiteListIPAddresses | <WhiteListIPAddresses name="name1">10.1.10.23</WhiteListIPAddresses> *See note |
Combining this setting with the BlacklistDomains setting is more effective. |
| BlackListSubnets | <BlackListSubnets name="name1"> |
|
| WhiteListSubnets | <WhiteListSubnets name="name1"> |
|
| BlockLocalIpAddresses | <BlockLocalIpAddresses>true</BlockLocalIpAddresses> |
|
| BlockLocalExclusions | <BlockLocalExclusions name="name2">k2.denallix.com:443</BlockLocalExclusions> |
|
*Remove the default XML comments from the configuration file or add new entries as per the examples above.
Troubleshooting
When you configure the settings in the appsettings.xml file, the configuration may be too restrictive causing it to block all requests to resources, or a specific solution now needs to convert a site to PDF which was originally not part of the configuration.
Depending on the resource that is blocked, you may see different behavior. If the main URL that is requested for conversion is blocked, one of the following errors may occur:
“The PDF could not be saved”
“The url is blocked or there is an issue with the SSL certificate for the site requested.”
If a resource like an image or an iframe is blocked, the conversion generates a PDF with everything it could load, but the blocked resources will not show, similar to what displays when a webpage cannot load a resource.
When a request is blocked, an error message is logged in the latest log file in [Program Files]K2K2 PDF Converter ServiceLogs folder. Use the error message in the log file to determine the reason for the block. Below is an example of an error message:
[2021-02-09 09:01:12][ERR][Host:][App:SourceCode.PdfConverter.Api][CID:][SID:][Path:][Src:]: Blocking loading of request due to rule:"WhiteList IpAddresses" and value:"13.107.42.14". Request to:"www.linkedin.com" with frame domain:"" IsMainFrame:False ResourceType:SubFrame TransitionType:AutoSubFrame Referrer:"simple.external.com"
| Color | Description |
| Yellow | The configuration node blocking the request |
| Pink | The value causing the block |
| Blue |
|
| Green | The type of resource the request came from |
| Gray | The site from where the request originated |



