Hi,
We are trying to impersonate a user accessing via a K2 SmartForm all the way trough to a 3rd party SQL Server.
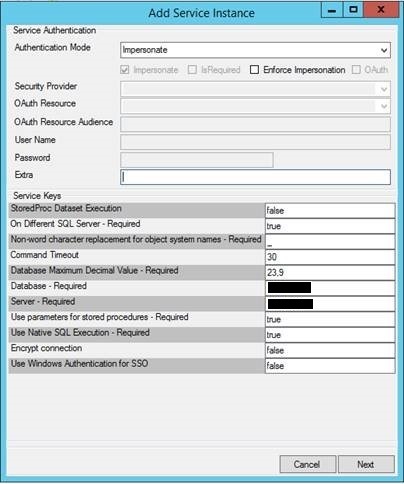
We are using windows authentication (not kerberos) and the SQL service instance is configured as seen in this screenshot in order to enable the K2 pass-through functionality and impersonation.
Running versions:
- .NET Framework v4.0.30319
- K2 Host Server Version: 4.16200.17215.5
- SQL Server 2016 (SQL Server 13.0.4446)
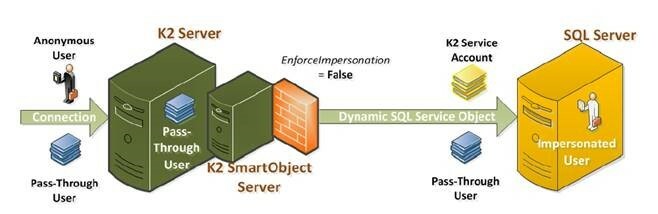
The K2 service account is sysadmin on the 3rd party SQL Server 2016
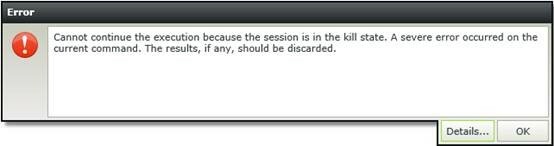
When we try to run the smartform in a web browser we get a kill state error message:
Running a sql server profile trace we can see that the underlying sql server error message is as follows:
”The connection has been dropped because the principal that opened it subsequently assumed a new security context, and then tried to reset the connection under its impersonated security context. This scenario is not supported. See "Impersonation Overview" in Books Online.”
Below is a screen shot from the trace showing the actual error:
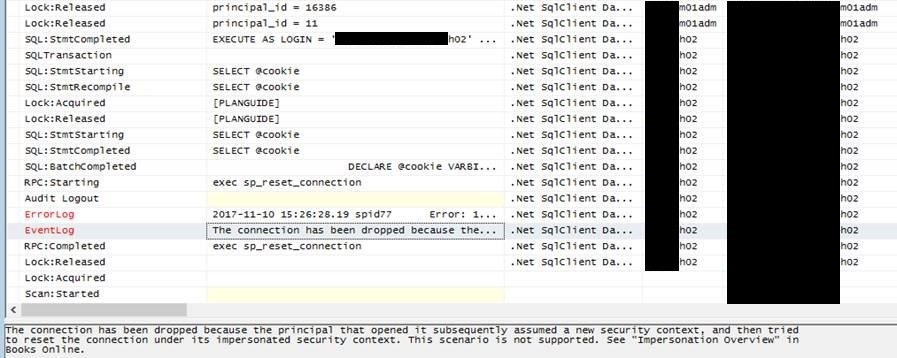
Account "m01adm" runs the HostServer instance, "h02" is the user that runs the smartform.
Any suggestions and/or tips is appreciated.
