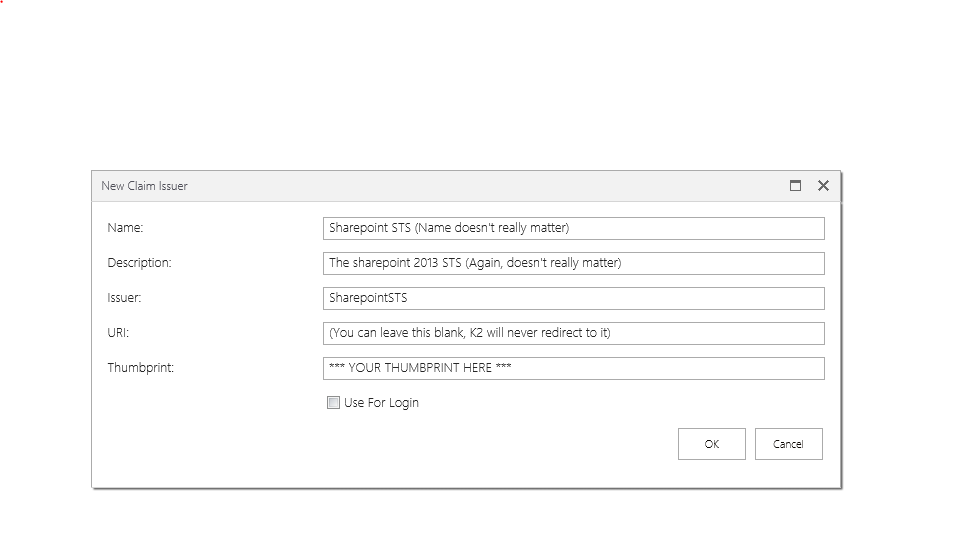
I have a project in SharePoint 2013 and we plan to interact with K2 Process by using K2 API in WCF. The WCF is deployed under sharepoint context _vti_bin. When opening the K2 connection from the wcf it throws an error "Value cant be null Parameter Name Token". This error suggest that claims authentication should be configured in K2, which I have already configured.
Base on this report
It seems like esp 2013 claims integration with K2 blackpearl is not supported, is it true? It stated that K2 suggested a manual fix by executing some script directly in K2 database.
Kindly suggest a way to integrate with K2 throgh API using WCF hosted in SharePoint 2013 _vti_bin. If possbile we call the WCF from SharePoint classic visual web part and not from app web part.
My Enviroment:
Windows Server R2
SharePoint 2013 Enterprise
K2 Blackpearl 4.6.9