Topic
When in Skuid adding AWS databases (Postgres, Microsoft SQL server, etc.), Skuid provides this guidance in an effort to assist in connecting to the database:
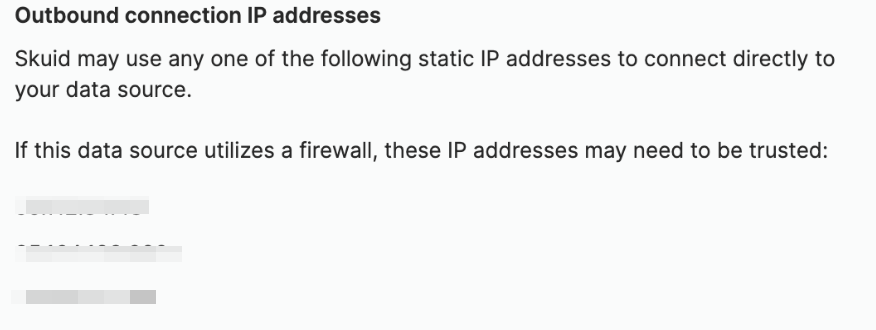
However, when navigating the AWS platform, users may find it difficult to navigate how to complete this process.
Resolution
This process can be completed via creating a VPC(Virtual Private Cloud) security group, creating inbound rules to allow Skuid’s recommended IP addresses to connect, then assigning that created VPC security group to your database in the RDS console.
Problem Details
Amazon manages traffic in Virtual Private Cloud via security groups. Security groups allow or deny specific inbound and outbound traffic at the resource level (such as an EC2 instance). When you launch an instance, you can associate it with one or more security groups. Each instance in your VPC could belong to a different set of security groups, giving the user more control over security if they are managing a number of instances.
Resolution Process
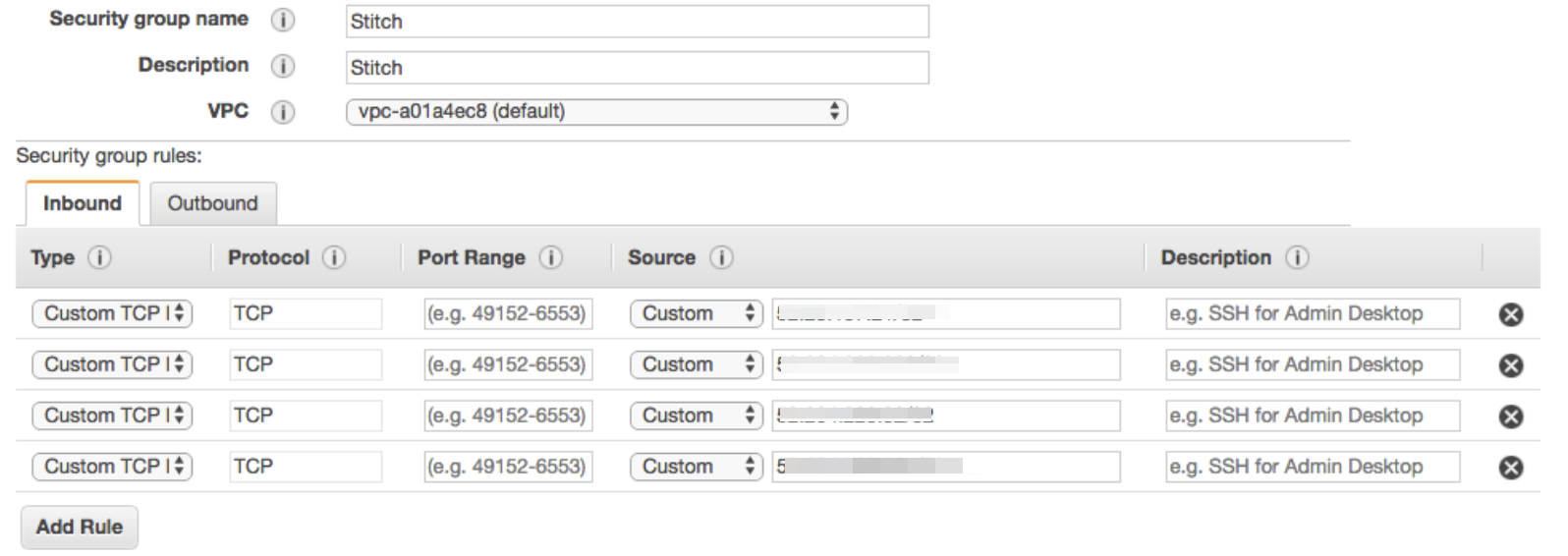
The outline on how to create a VPC security group within AWS can be found here. When creating the VPC security group, you can also create inbound rules for the IP addresses to allow Skuid to connect:
Note
You may have to add your own IP addresses to the list as well.
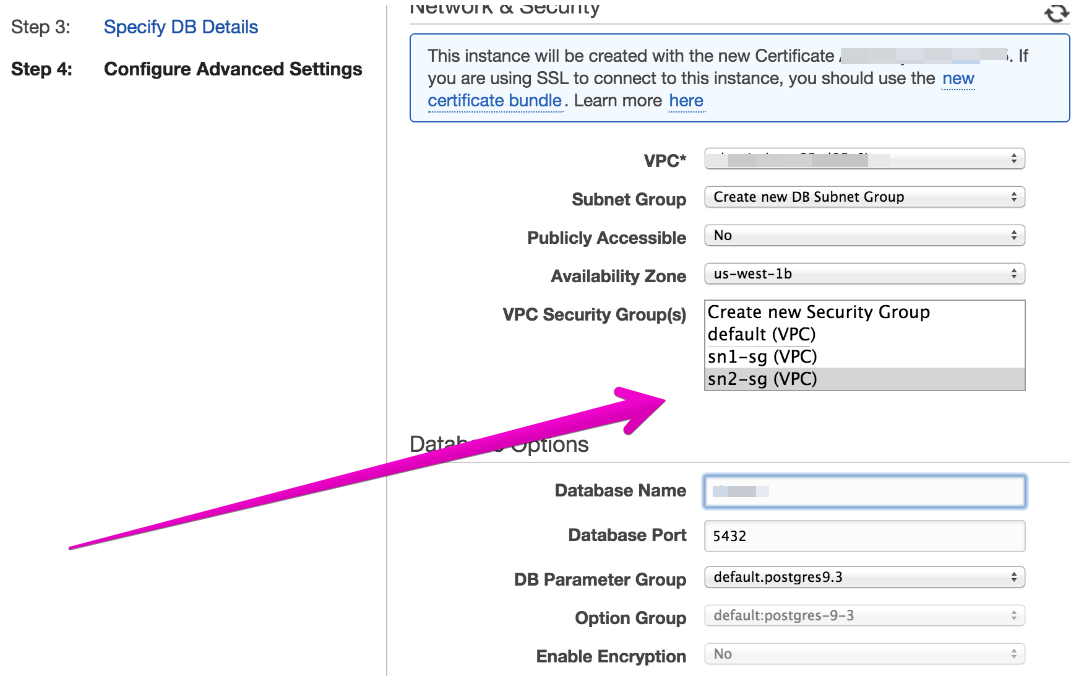
Then when configuring the database, chose the security group that was created:
Outcome
Upon completion of this process the user was able to connect to their AWS Postgres instance without issue.
Additional Information
Most of the major cloud providers follow a similar hierarchy in their cloud instances. So when working with other providers Microsoft Azure, Oracle, etc. you may have to follow a similar process to connect to their databases.
Get help with an issue
- Ask in the Skuid question forum.
- If you have a support entitlement, ask your question in Nintex Customer Central.
