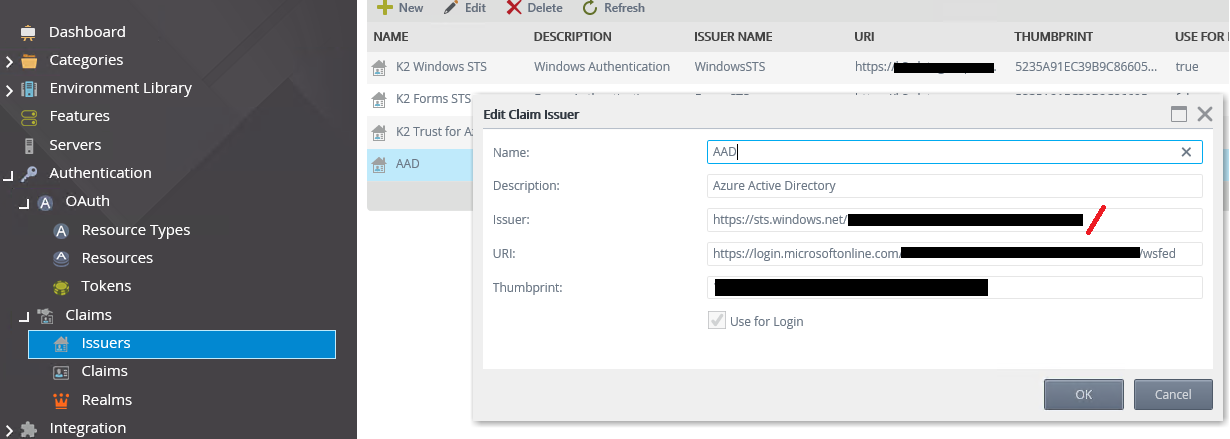
Hi
After configuring oauth and the claims issuer in designer I am unable to log in fully to designer using my AAD account, redirects fine to the Azure login but after this I get the error
WIF10201: No valid key mapping found for securityToken: 'System.IdentityModel.Tokens.X509SecurityToken' and issuer: 'https://sts.windows.net/xxxx-xxxx-xxxxx
I have checked the Thumbprint against the accesscontrol.windows.net certificate and this seems fine, I believe this to be the current 92B88C3DD981BF1EBCB244FCFA63C007706C79E0, a couple of alkthroughs had used this one 3464C5BDD2BE7F2B6112E2F08E9C0024E33D9FE but I believe that to be expired now.
Has anyone else had a similar issue.
Thanks
Adam