Symptoms
Often when you have multiple environments pointing to the same SharePoint environment. Issue can arise because of certificates being mismatched between K2 and SharePoint environment. This problem in particular can interfere with a multitude of K2 for SharePoint functionalities as well as preventing the registration of the K2 for SharePoint App. An example symptom of this problem can be seen when a user would try to register the SharePoint app:
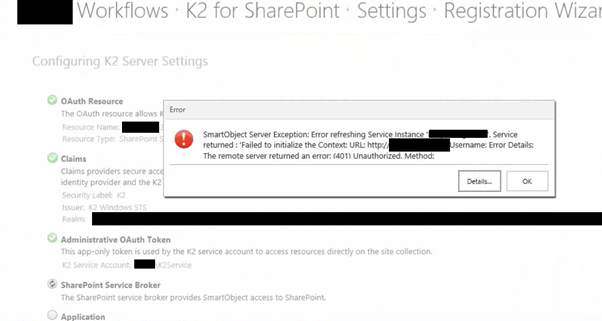
This is because the setup manager on SharePoint has registered 1 specific SecurityIssuer for the last server that was configured. So in a sence it is configured to use the certificate from the K2 server that was last configured in SharePoint.
For example if K2 for SharePoint was configured first to use the K2 Production environment and then rerun to add the K2 Development environment the installer creates a security issuer for the last created one and removes the other. The way to fix it is to make sure all servers have the same certificate.
Diagnosis
To resolve this issue you must first verify that the Trusted Token Issuer in SharePoint exists and you can verify that the associated certificate is in the trusted root authority. You must also ensure that the thumbprint for both the Trusted Token Issuer and Trusted Root Authority match.
From the SharePoint Management Console(As Administrator On SharePoint Server):
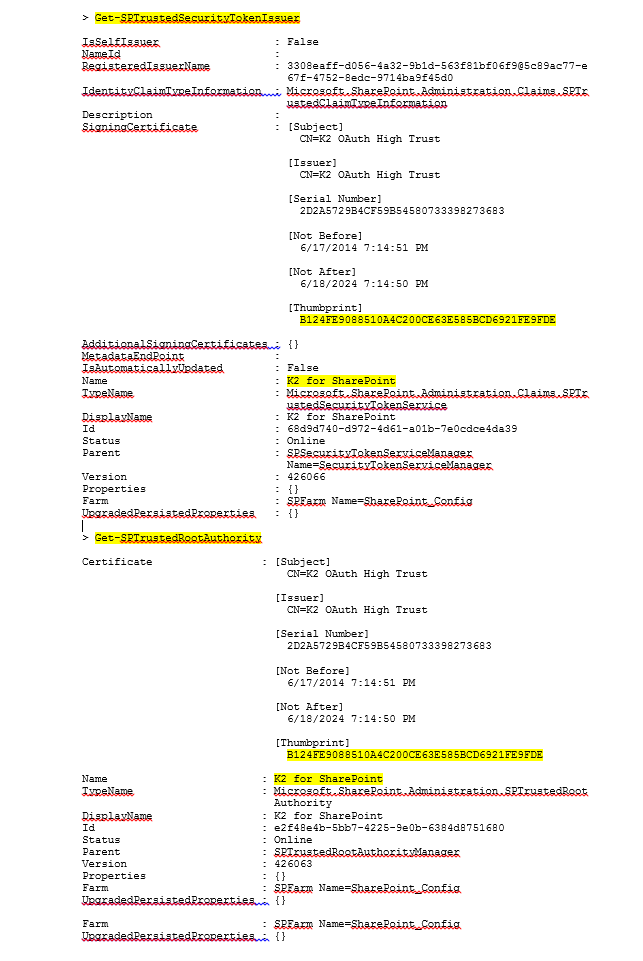
Once you have verified that the Token issuer has been registered correctly using the K2 OAuth High Trust certificate, you can start repairing the OAuth Certificates in your K2 environments.
The way to fix it is to make sure all servers have the same certificate.
Solution
Once you have verified that the Token issuer has been registered correctly using the K2 OAuth High Trust certificate, you can start repairing the OAuth Certificates in your K2 environments.
-
- First delete the token issuer and certificate from SharePoint, you can do so by running the following scripts using PowerShell.
Remove-SPTrustedSecurityTokenIssuer -Id "K2 for SharePoint"
Remove-SPTrustedRootAuthority -Id "K2 for SharePoint"
-
- Truncate the following Table
TRUNCATE TABLE TRUNCATE TABLE OK2].AAuthorization].>OAuthToken] Once the environment have been cleared off all relevant token’s and certificates. You will need to run the DB Certificate Manger to ensure that all the certificates on the multiple K2 environments match so they can communicate with the SharePoint Server. For more information on the DB Certificate Manager please refer to the following KB article: Then after you have ran the Certificate Manager in accordance with the KB article, run the SharePoint AppDeployment.exe. This will re-create the correct SPTrustedRootAuthority and TokenIssuer configuration in SharePoint, using the new certificate generated by K2 Verify at this point that the Token issuer and trusted root authority certificate is correctly added as in the beginning of this document. The certificates should match and registration wizard should run through correctly. It may help at this point, when running the registration wizard, to enable full debug logging on K2 HostServer. There are debug messages logged when the app only token is issued which may help with further investigation.

