Symptoms
When upgrading environment to K2 4.6.8 or newer configuration analysis fails with the following error:
Analysis Result: Failed.
Constrained delegation is not enabled for the Active Directory account: %K2_SERVER_NAME%
The K2 Windows Token Service is a Windows Identity Foundation (WIF) feature that extracts UPN claims from SAML tokens and generates Windows security tokens. This allows K2, as the relying party, to impersonate a claims user for access to a line of business system, such as SQL.
Important: If you have configured Kerberos in your environment, a domain administrator must configure constrained delegation in Active Directory. For more information see the link below:
How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0 (MSDN)
Duration: 0 seconds
Sample error message screenshot:
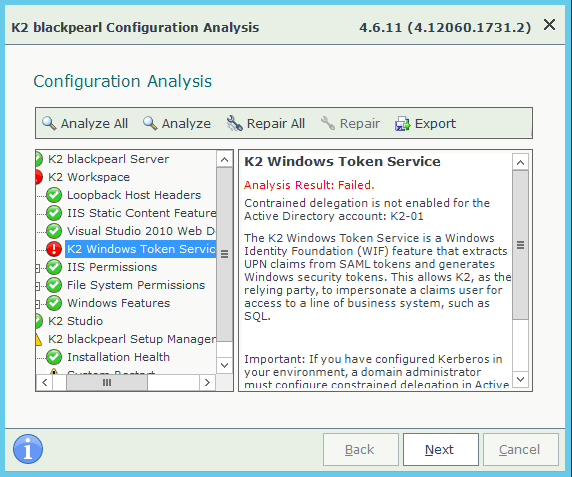
Error mentions Kerberos constrained delegation but it may be the case that this was configured previosly configured when version of K2 older than 4.6.8 was installed and there was no warnings in configuration analysis for these older K2 versions.
Diagnoses
In K2 4.6.8 K2 Windows Token Service is introduced which is installed on the servers where the K2 Designer, K2 smartforms Runtime and K2 View Flow components are installed. This service is used to convert claims tokens to Windows tokens for off-box authentication and impersonation that requires a Windows token, such as SQL Server. The K2 Windows Token service runs under the local system account.
Even if you configured Kerberos constrained delegation previously, you additionally need to add the constrained delegation settings required for the K2 Windows Token Service.
Resolution
This question and respective constrained delegation configuration is covered in following K2 KB article: KB001607 – Delegation Settings to enable K2 Windows Token Service to impersonate using Kerberos
To avoid possible misunderstanding of official KB above what you have to do is to set configuration settings as depicted on screenshot from official KB:
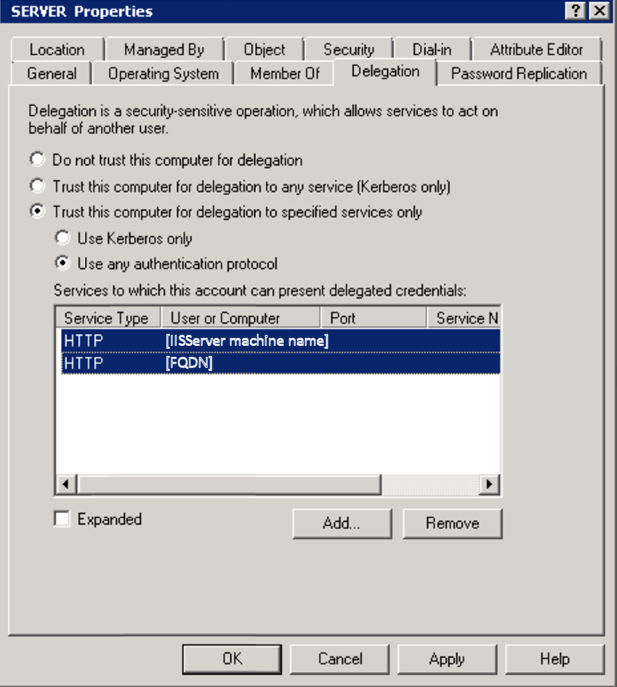
You have to locate your K2 server in Active Directory Users and Computers snap-in select Properties and on Delegation tab set "Trust this computer for delegation to specified services only" + "Use any authentication protocol", then click on add and select your K2 server (i.e. the same server you setting properties for) click add and select "http" as a service type.
You need only once select your server and HTTP service - it will create entries both for machine name and machine FQDN - you just need to tick "Expanded" checkbox to see this (in this respect screenshot above is a bit misleading/confusing).
In case you have multiple K2 servers you repeat this operation for each of them. Each server only needs to delegate HTTP service types TO ITSELF because the service is installed locally on that server.

