"MapToWindows: Failed to map to windows" error appears in event logs
kbt146511
PRODUCTIssue
This error appears in the event logs:
MapToWindows: Failed to map to windows: System.ServiceModel.FaultException`1[System.ServiceModel.ExceptionDetail]: WTS0003: The caller is not authorized to access the service. (Fault Detail is equal to An ExceptionDetail, likely created by IncludeExceptionDetailInFaults=true, whose value is: System.UnauthorizedAccessException: WTS0003: The caller is not authorized to access the service. at Microsoft.IdentityModel.WindowsTokenService.CallerSecurity.CheckCaller(WindowsIdentity callerIdentity) at Microsoft.IdentityModel.WindowsTokenService.S4UServiceContract.PerformLogon(Func`1 logonOperation, Int32 pid) at Microsoft.IdentityModel.WindowsTokenService.S4UServiceContract.UpnLogon(String upn, Int32 pid) at SyncInvokeUpnLogon(Object , Object[] , Object[] ) at System.ServiceModel.Dispatcher.SyncMethodInvoker.Invoke(Object instance, Object[] inputs, Object[]& outputs) at System.ServiceModel.Dispatcher.DispatchOperationRuntime.InvokeBegin(MessageRpc& rpc) at System.ServiceModel.Dispatcher.ImmutableDispatchRuntime.ProcessMessage5(MessageRpc& rpc) at System.ServiceModel.Dispatcher.ImmutableDispatchRuntime.ProcessMessage41(MessageRpc& rpc) at System.ServiceModel.Dispatcher.Immutable...).
Symptoms
The symptoms consist of the above exception appearing in the event viewer and end user/administrator thinking there is an underlying issue somewhere in the configuration. The text below specifies how to get rid of the exception given the circumstances.Resolution
If the exception message appears, the end user/administrator needs to identify whether the connected windows user needs to be used, when connecting to any other LOB system like SAP, SQL, etc. where that system only accepts "pure windows".
(I.e. SharePoint 2013 and up uses OAuth so no need for windows authorisation to flow through).
If the end user/administrator sets all service instances that connect to these LOB systems to use Service Account authentication, then they do not need "pure windows" authorisation to flow through. This means the K2 Claims to Windows token service doesn’t need to be configured. Also, if that is the case, the MapToWindows setting in the SmartForms web.config file can be switched off.
If you set MapToWindows to off, don't forget to un comment the line 6 of the web.config:
<section name="sourceCode.identityModel" type="SourceCode.Security.Claims.Web.Configuration, SourceCode.Security.Claims.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=16A2C5AAAA1B130D"/>
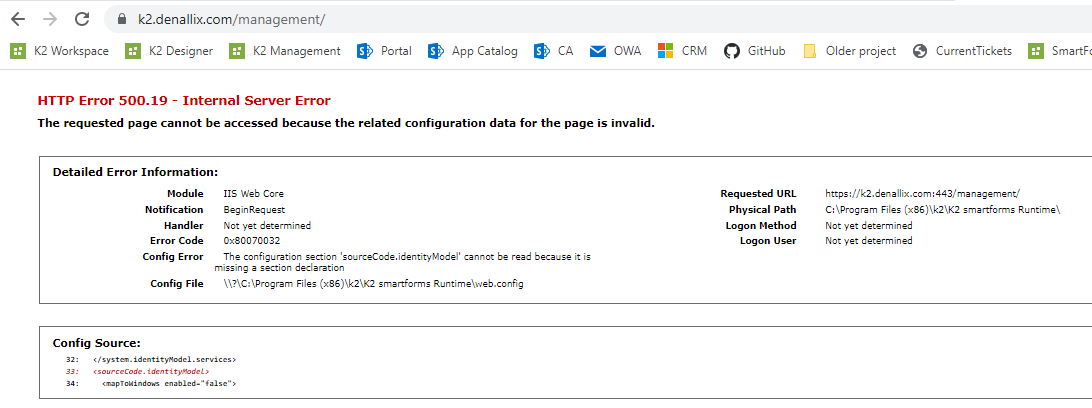
If you don't do it, you will have the following error:
The configuration section 'sourceCode.identityModel' cannot be read because it is missing a section declaration