Howdy,
I’m wondering if anyone has come across this issue before or might know a solution;
A handful of our workflows have assigned tasks that are sent to shared mailboxes:
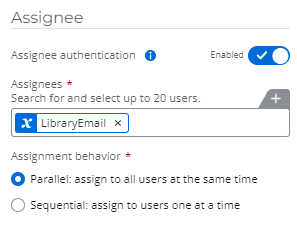
However when the task email is received in the shared mailbox, and a person that has access to that shared mailbox, tries to open the task URL, they receive an access denied error in their web browser:
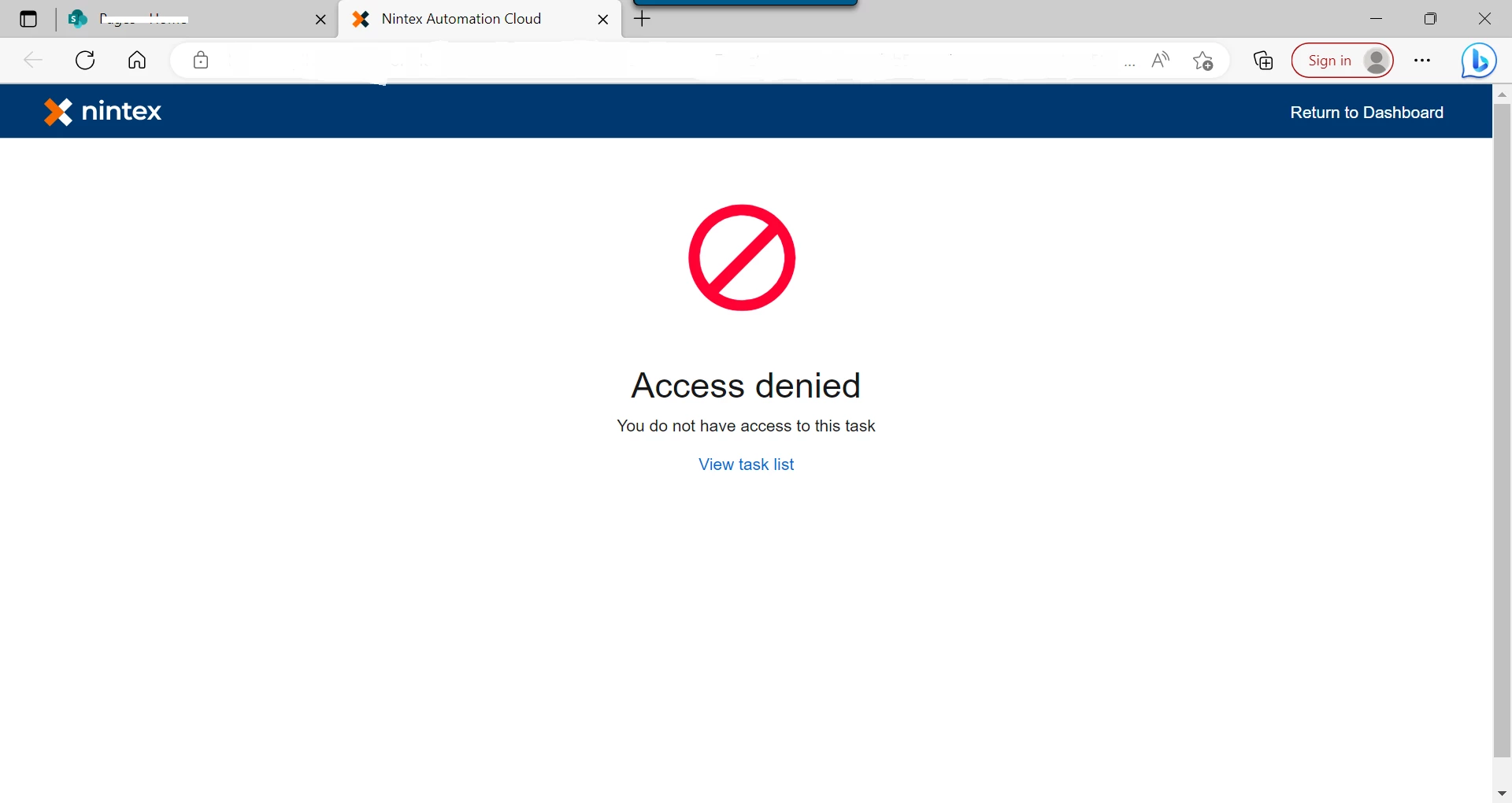
I presume this is because the task is assigned to the shared mailbox email, and not the user email, so access is rejected?
We could get around this issue by disabling “Assignee Authentication” on the task itself, however we require assignee authentication as the approver details are captured for audit purposes.
Is this expected behaviour for shared mailboxes and tasks? Or is there a fix for allowing users to access a task that is sent to a shared mailbox?
Best answer by SimonMuntz
View original


