OAuth resources and the protection of sensitive information
KB003698
PRODUCTIntroduction
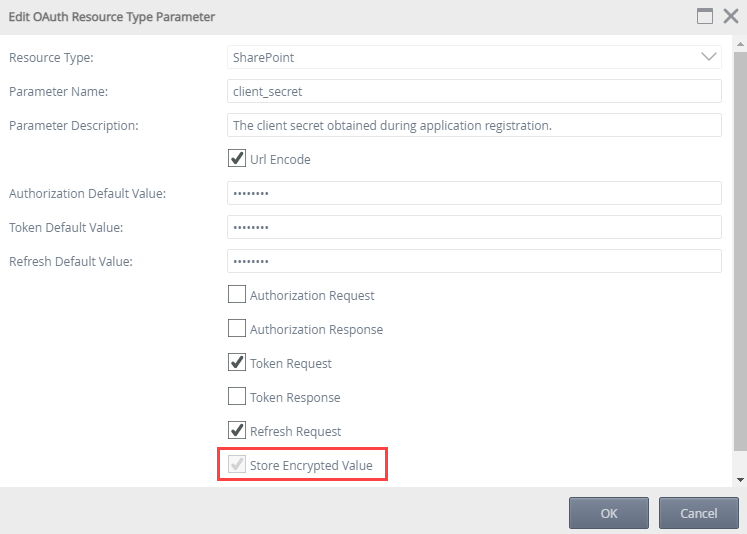
For added security, a new feature is introduced with K2 Five 5.6 to handle sensitive information for OAuth resources. OAuth resource configuration often contains highly sensitive information, such as a client_secret, which is a security threat if the value is compromised. To protect these sensitive values, a new option is now available in the OAuth Resource Type Parameter configuration in K2 Management called Store Encrypted Value.
Implementation
When you select this option for a parameter on the resource type, all values associated with this parameter are encrypted in the K2 database and masked (hidden) with dots in the user interface. When typing new values into the fields on the configuration screen, the values display in clear text, and when you save it, dots replace the values in all user interfaces. The encryption and masking of the values have no impact on using the OAuth resource. OAuth flows still use the values as before in an unencrypted way. The option only affects how it is stored in the database and how it is shown in user interfaces.
When the option is selected, it applies to the following values:
- OAuth resource type parameter default values - Authorization, token, and refresh default values
- OAuth resource parameter values linked to the specific OAuth resource type parameter - Authorization, token, and refresh values
- OAuth resource parameter token replacement values linked to the specific OAuth resource type parameter
How does this feature affect existing OAuth resource type parameters?
In K2 Five 5.6, this feature is selected by default on the resource types and parameters listed below, and values are automatically encrypted.
- Cloud Storage: apiSecret, accountId
- Dynamics 365 for Sales: apiSecret
- Microsoft Online: client_secret
- Microsoft Online AppOnly: client_secret
- Salesforce: client_secret
- SharePoint: client_secret
When you create new OAuth resource types after the upgrade to K2 Five 5.6, ensure to select this option if you require the parameter to be encrypted.

