Admin consent required before the next upgrade (Update 16) can be applied
KB003673
PRODUCTMicrosoft is deprecating Azure AD Graph API in June 2022, and as of June 30th, 2020, stopped adding new features to the API. See these Microsoft articles for more information:
- Migrate Azure Active Directory (Azure AD) Graph apps to Microsoft Graph
- Azure Active Directory (Azure AD) Graph to Microsoft Graph migration FAQ
Microsoft strongly recommends upgrading to Microsoft Graph API to access Azure AD APIs or APIs from other Microsoft services. Nintex K2 Cloud OAuth resources requiring access to the https://graph.windows.net API (Azure AD Graph), must be updated to use https://graph.microsoft.com (Microsoft Graph) as part of the migration from Azure AD Graph to Microsoft Graph. Nintex K2 Cloud Update 16 includes the code fixes necessary for this migration.
After the upgrade of your Nintex K2 Cloud environment to Update 16, the OAuth resources that require access to AAD Graph API will be updated to use Microsoft Graph API instead.
This will affect Package and Deployment tool and the workflows using the Azure Active Directory broker. These workflows can enter a failed state if the workflow executes a step that uses the broker after upgrade, but before a Global administrator in your organization re-consents to the Microsoft Graph permissions. These workflows will have to be manually repaired after upgrade and re-consent.
This will also let your users continue to package and deploy your solutions.
Consent to the Microsoft Graph permissions
Follow these steps before the upgrade to Update 16, to grant Admin consent to the Microsoft Graph permissions.
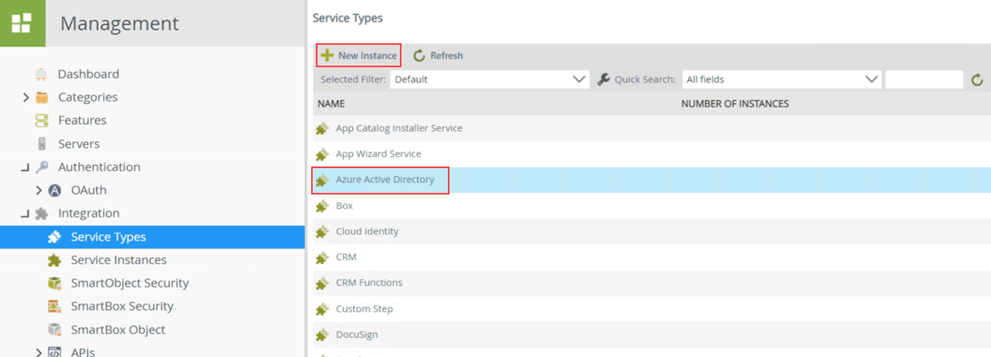
- In K2 Management, browse to Integration > Service Types and select the Azure Active Directory service type. Click New Instance.
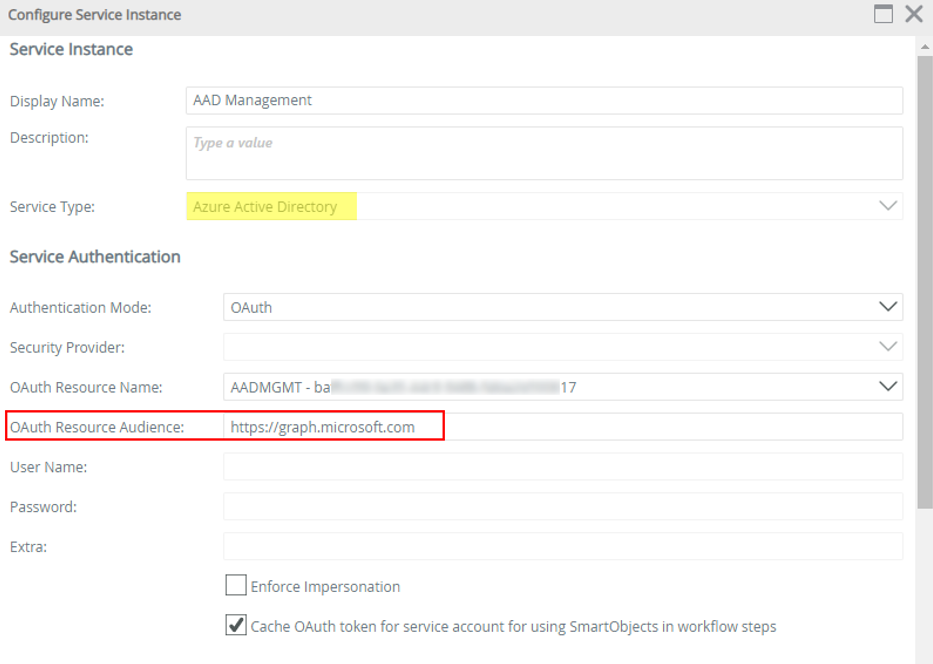
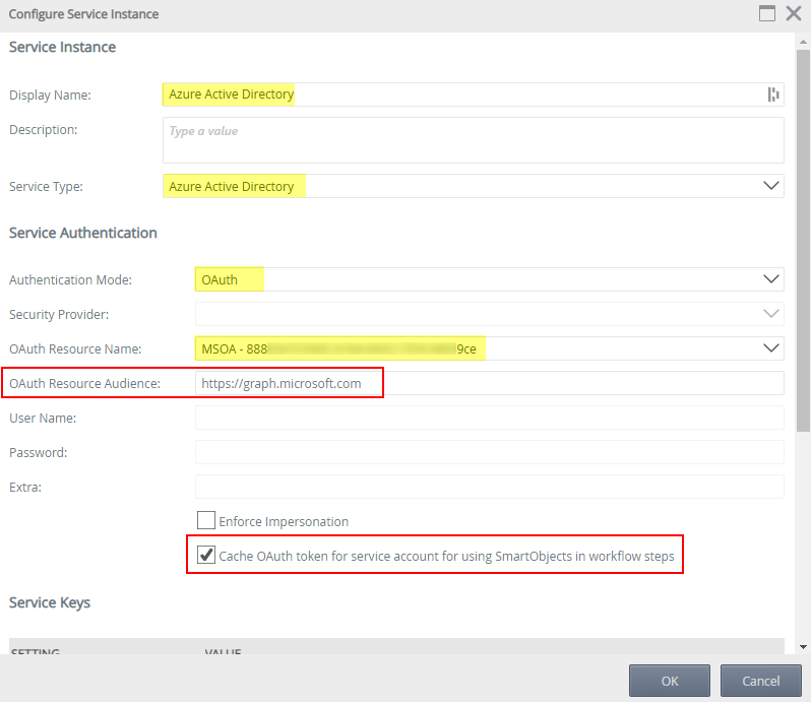
- Configure the Service Instance as described in the Service Instances topic of the Nintex K2 Cloud user guide but make sure to enter https://graph.microsoft.com as the OAuth Resource Audience. You must also tick the checkbox “Cache OAuth token for service account for using SmartObjects in workflow steps”
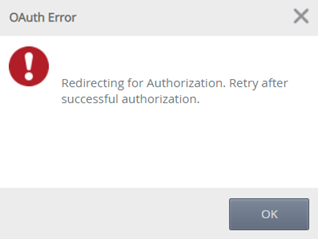
If you have previously consented to the new permissions and then run through this re-consent flow, you will not see the OAuth error, or permissions page described below in steps 3 and 4.
- When you click OK on the Configure Service Instance form, the OAuth Error dialog shows. Click OK again to be redirected for authorization.
- Sign in with your Global administrator credentials and Accept the permissions request to continue. Since permissions required for Azure AD Graph API differ from those for Microsoft Graph API, you will be consenting to similar permissions scopes for backward and future compatibility. For more information, see the topic Applications for integrating with third-party technologies in the Nintex K2 Cloud help documentation.
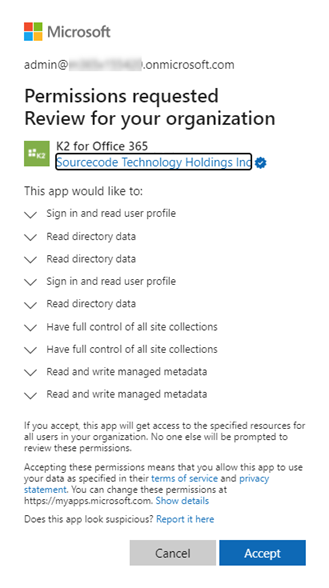
- You are redirected to the Authorization Successful page, at which point the new Microsoft Graph resource token is created (if it didn't exist). Close the tab to return to the K2 Management site.
- You are returned to the Service Instance registration page after the token is created. Click Cancel as there is no need to create a new Service Instance after completing the consent flow.
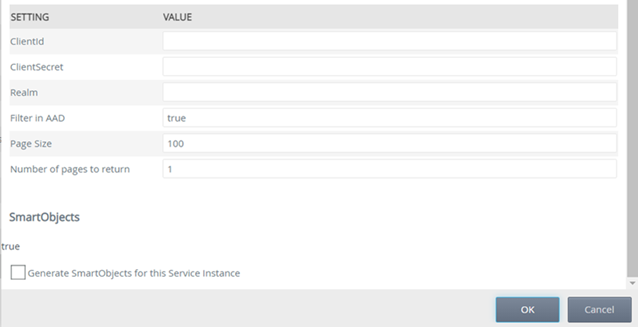
- Repeat the above steps (1-6) for the AADMGMT resource if used. Make sure to select AADMGMT as the OAuth Resource.
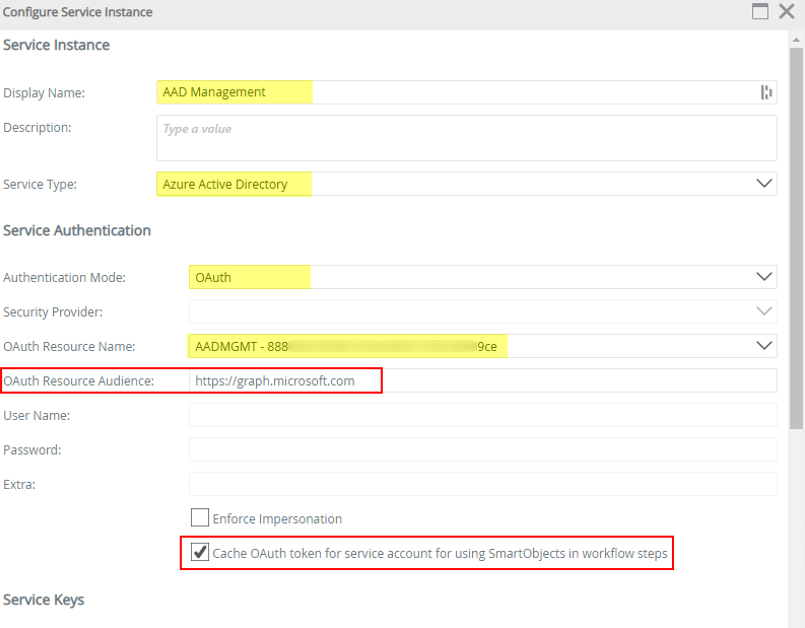
Post Upgrade Steps
Follow these steps after the upgrade to Update 16, in order to switch existing service instances to use https://graph.microsoft.com (Microsoft Graph API).
1. In K2 Management, browse to Integration > Service Instances and select the service instance using Azure Active Directory service type. Click Edit.
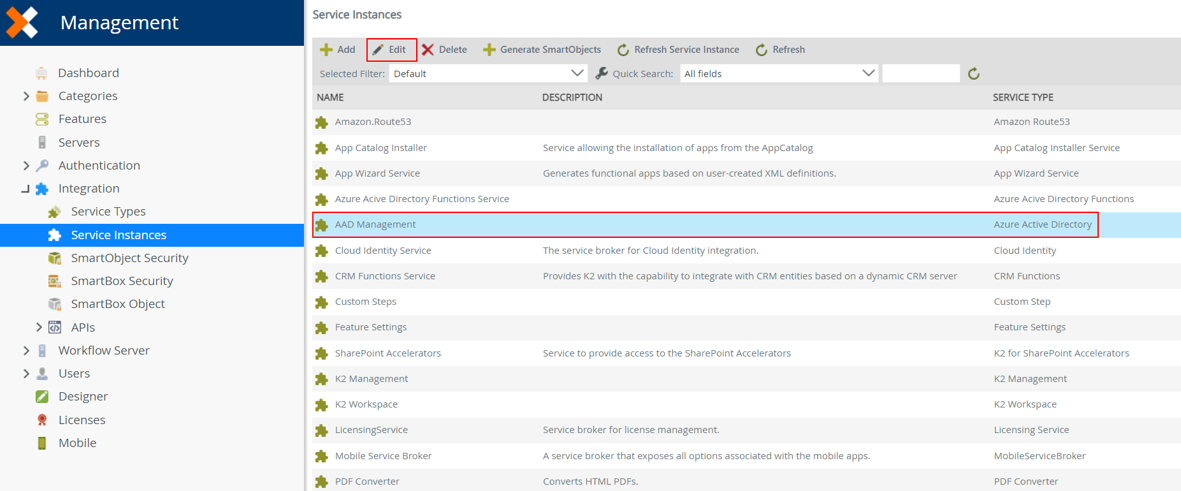
2. Update the OAuth Resource Audience to use https://graph.microsoft.com and click OK.