We are thinking of making a new application where part of the functionality will be creating and editing AD Users and groups. I am wondering what our best options would be for our DEV and TEST environments, since these all share the same AD environment as PROD.
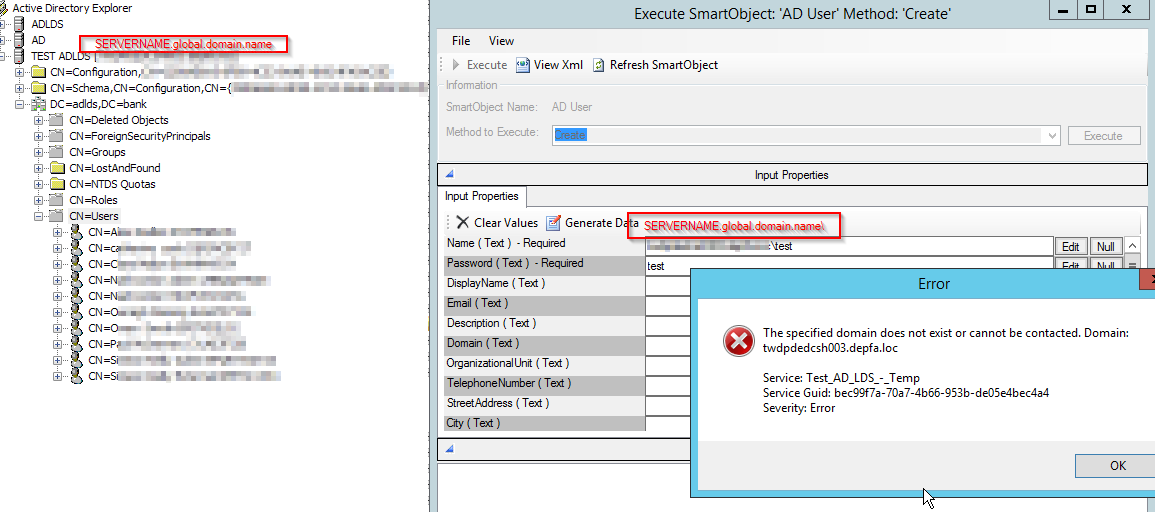
Would AD LDS be a good option? And has anyone gotten AD LDS to work with the Account Management Service Instance? I was able to create a Account Management service that pointed to an AD LDS instance, but on executing Create User I always get an error message - "The LDAP server is unavailable".
For the Create User - Name property in AD LDS I've tried servername.fqnusername, servernameusername, servername username, and I always seem to get the same result.
Best answer by ElvisJacob
View original


